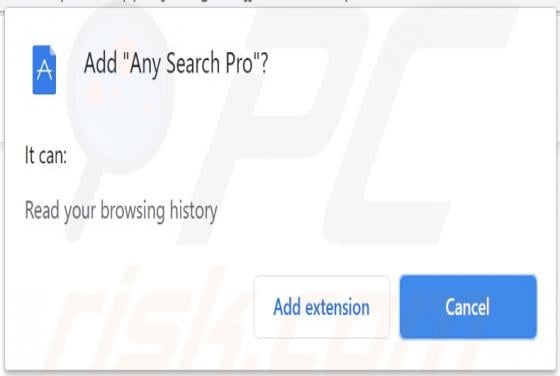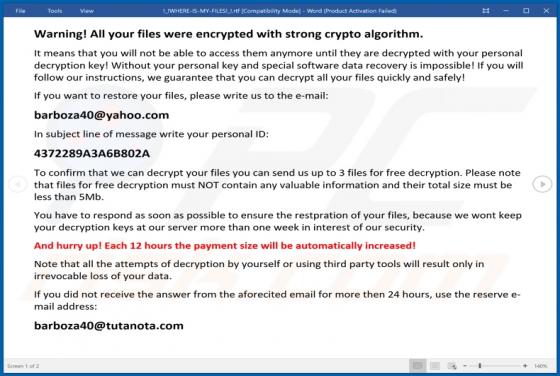
Barboza Ransomware
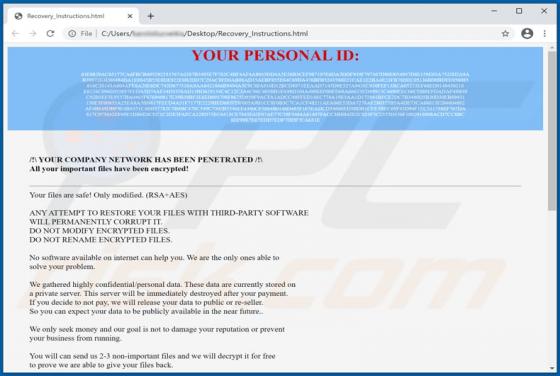
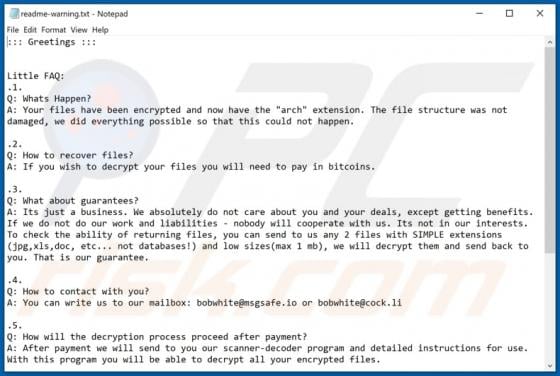
Belonging to the Matrix ransomware family, Barboza is a malicious program designed to encrypt data and demand payment for decryption. The files stored on the infected system are rendered inaccessible, and victims receive ransom demands for access recovery. When Barboza ransomware encrypts, files