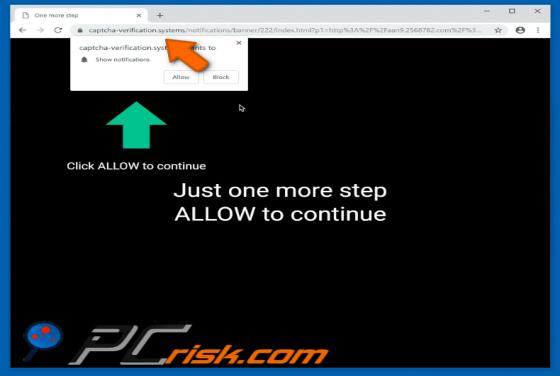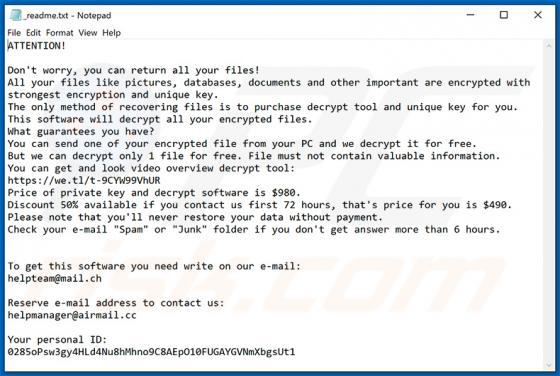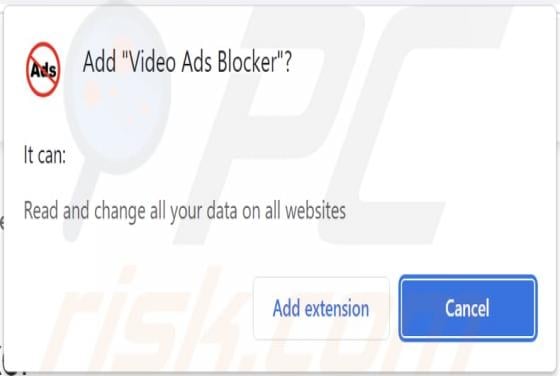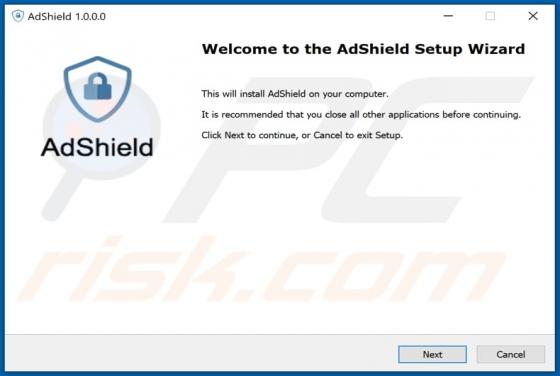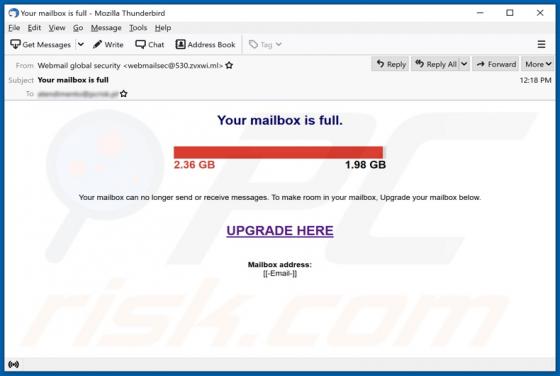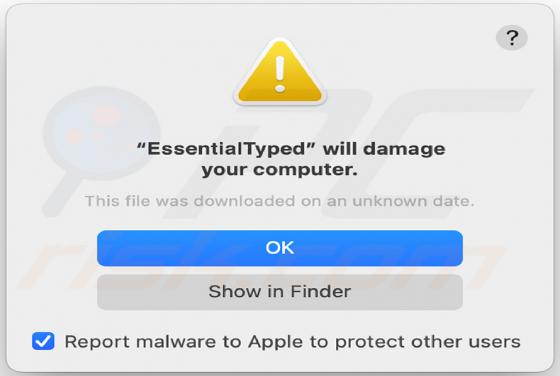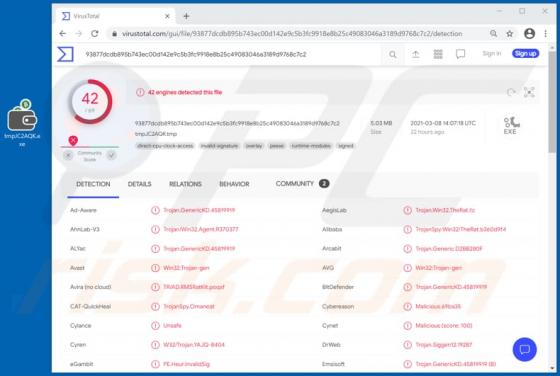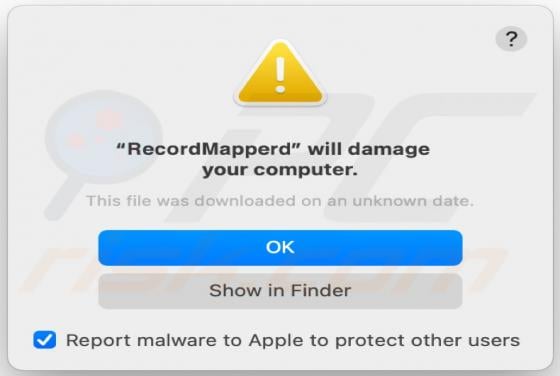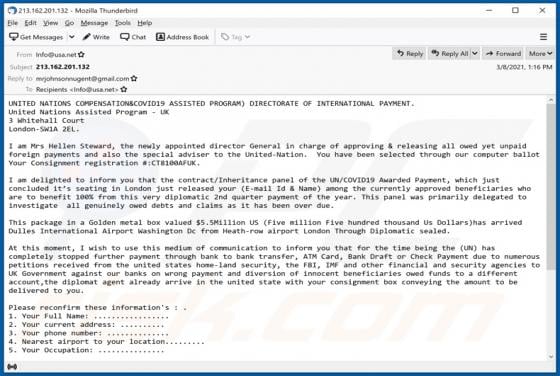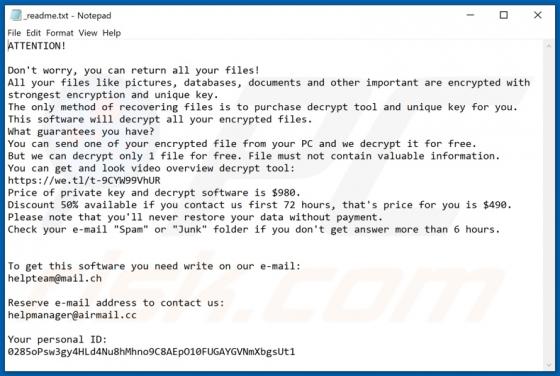
Tirp Ransomware
Tirp is a malicious program, which is part of the Djvu ransomware family. This malware operates by encrypting data and demanding payment for decryption tools/software. I.e., files affected by Tirp ransomware are rendered inaccessible, and victims are asked to pay a ransom to recover access to them