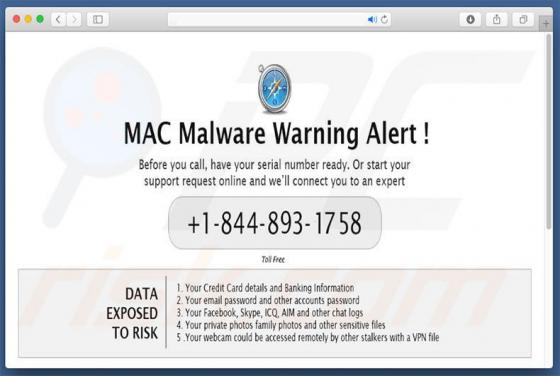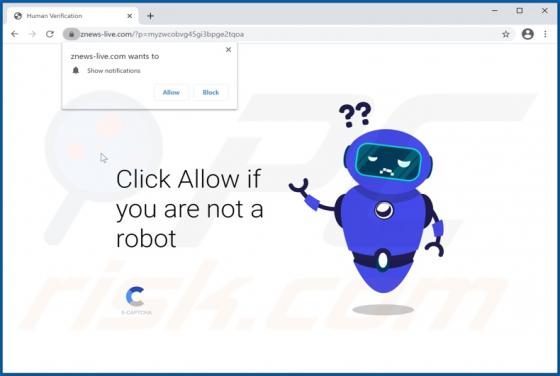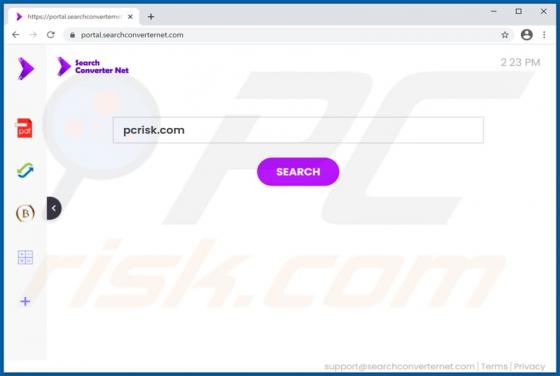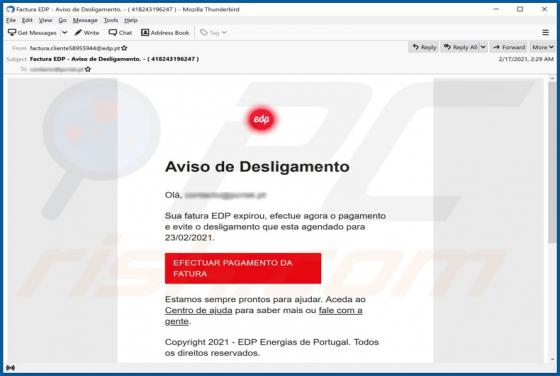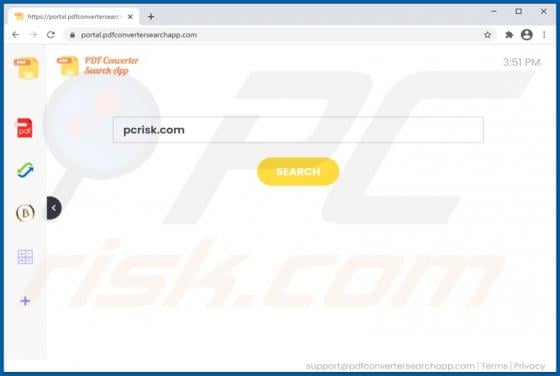
PDFConverterSearchApp Browser Hijacker
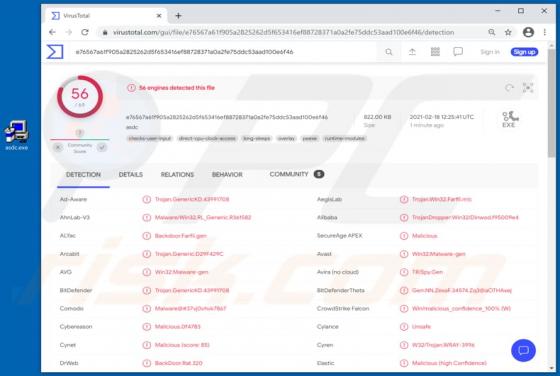
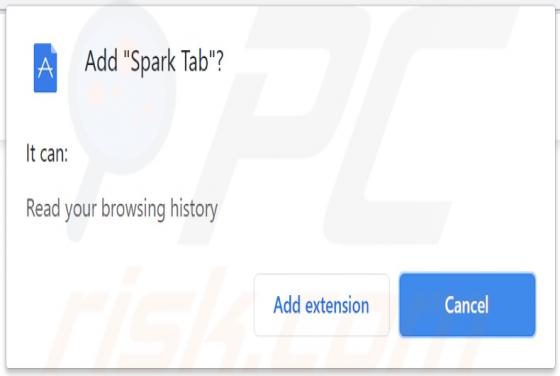
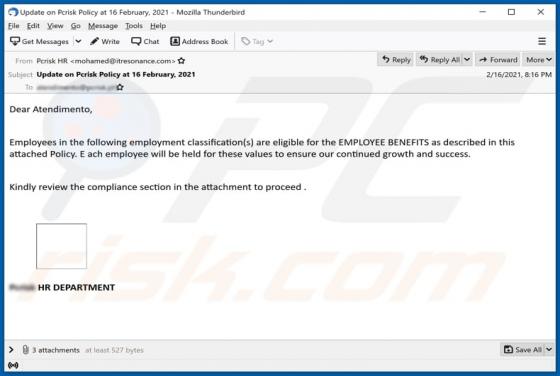
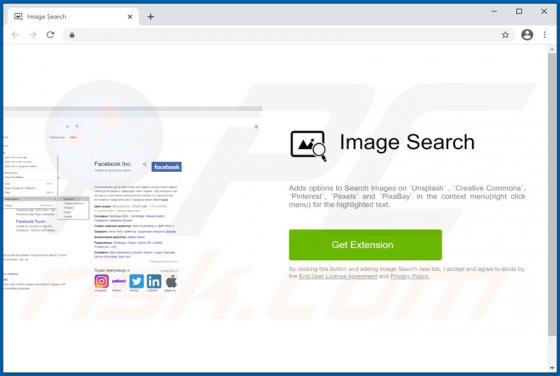
PDFConverterSearchApp is a typical browser hijacker: it alters specific browser's settings without the user's permission. It changes them to pdfconvertersearchapp.com, an address of a fake search engine. Also, it is likely that this app collects various data relating to user's browsing activities.