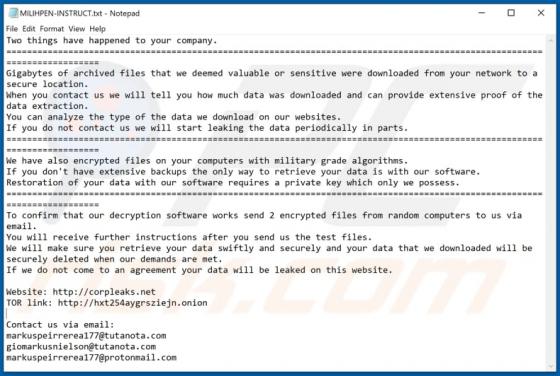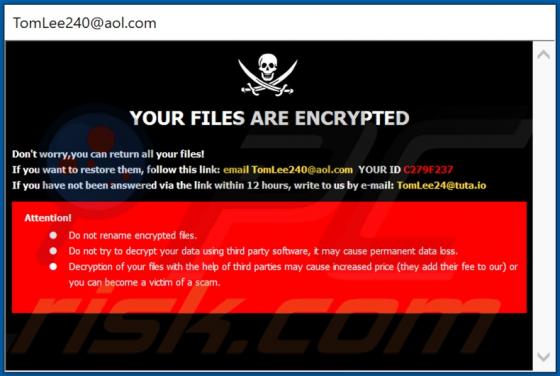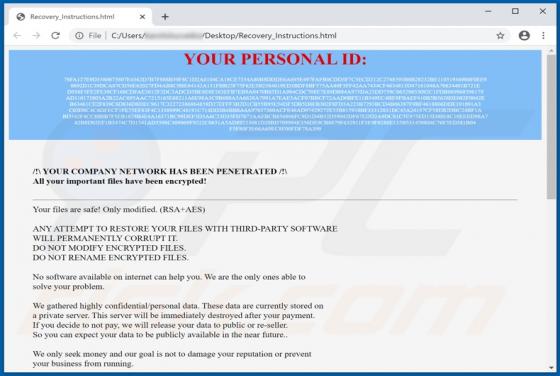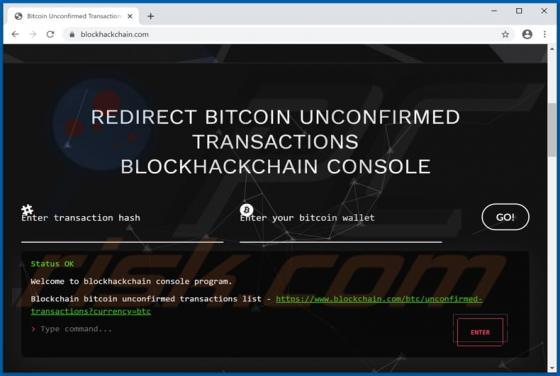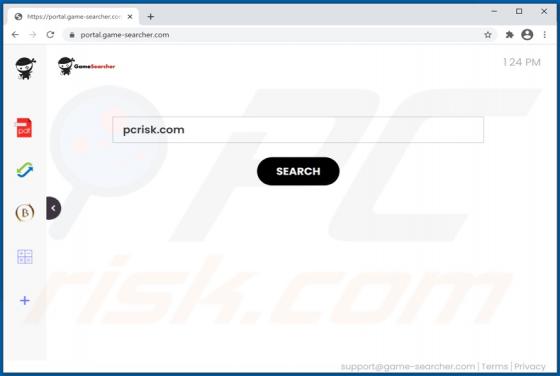
GameSearcher Browser Hijacker
GameSearcher is dubious software classified as a browser hijacker. It operates by making alterations to browser settings to promote game-searcher.com (a fake search engine). Additionally, GameSearcher collects browsing-related information, which makes it a serious privacy concern. Due to the dubi