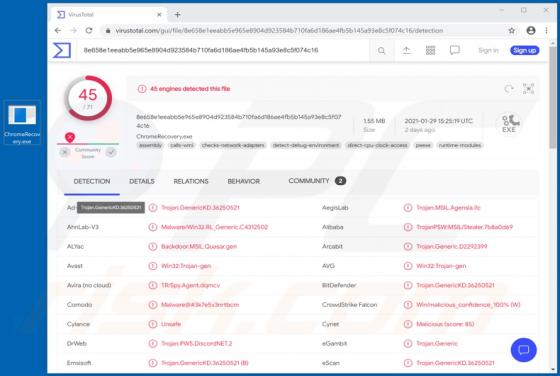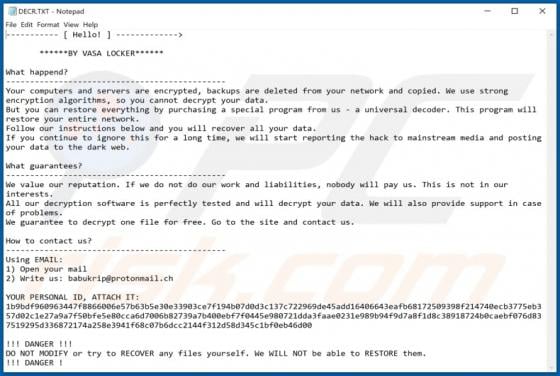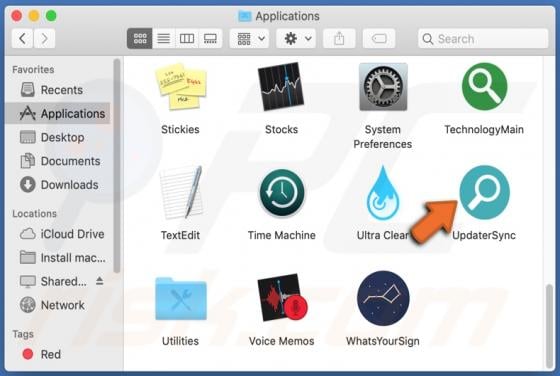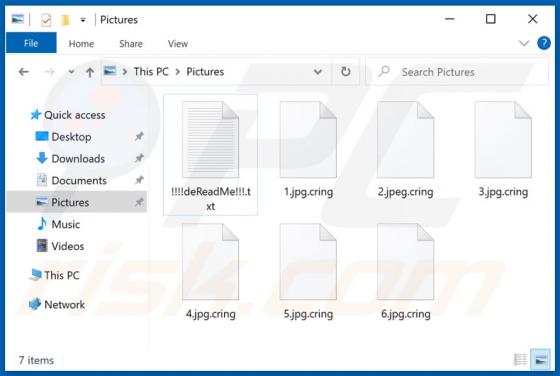
OriginalModule Adware (Mac)
People do not often download or install the OriginalModule app intentionally, since its installer is disguised as the Adobe Flash Player installer. Therefore, OriginalModule is categorized as a potentially unwanted application (PUA). This app is designed to modify browser settings (to promote a