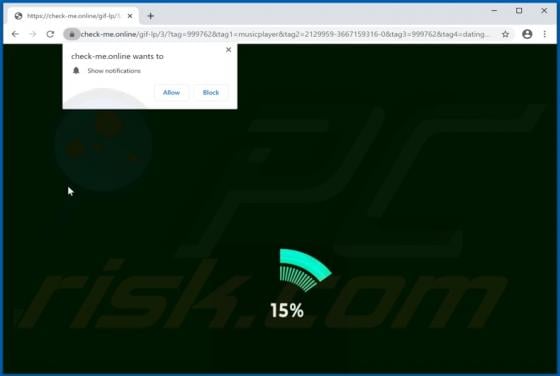
Check-me.online Ads
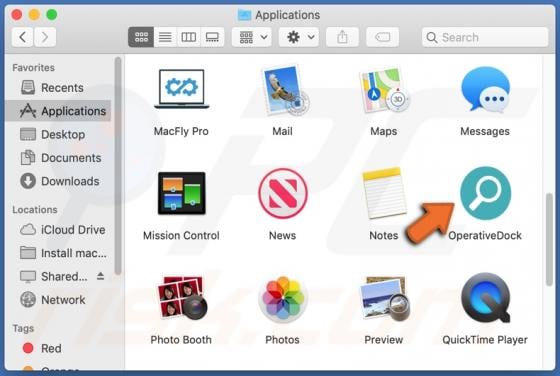
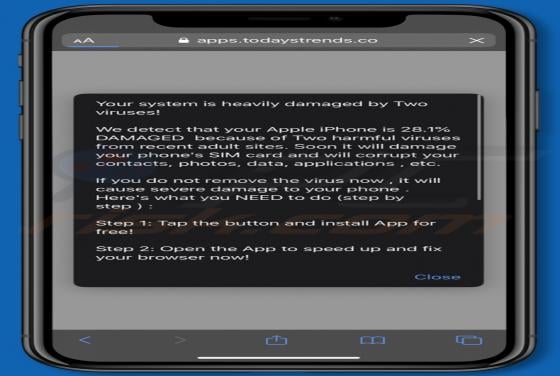
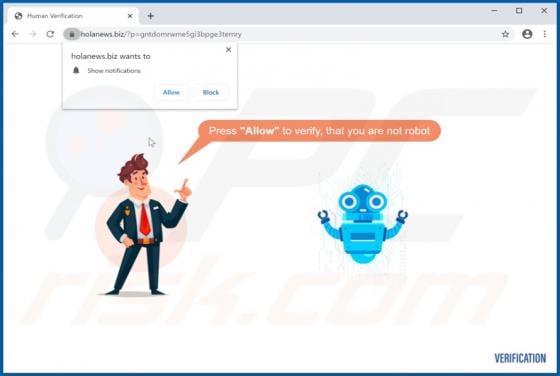
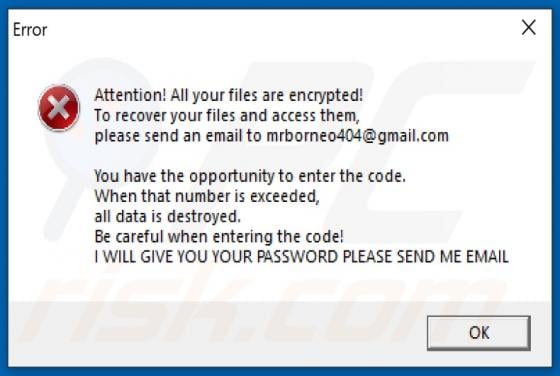
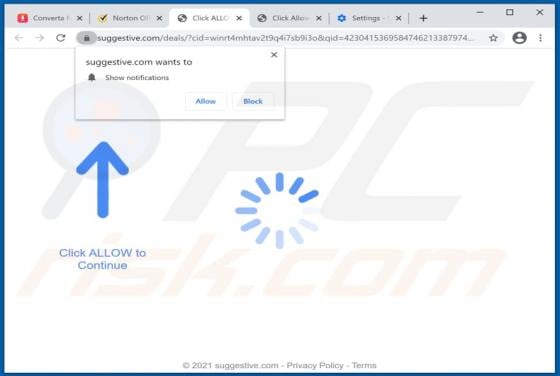
check-me[.]online is an untrusted website designed to present visitors' with dubious content and/or redirect them to other bogus and malicious pages. There are thousands of these rogue sites on the web - suggestive.com, purplemedia.biz, and luckhours.com are just some examples. Visitors rarely en