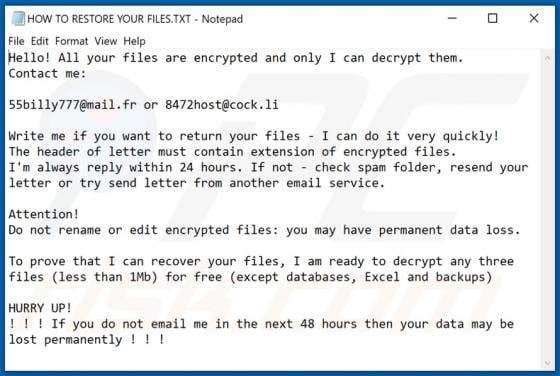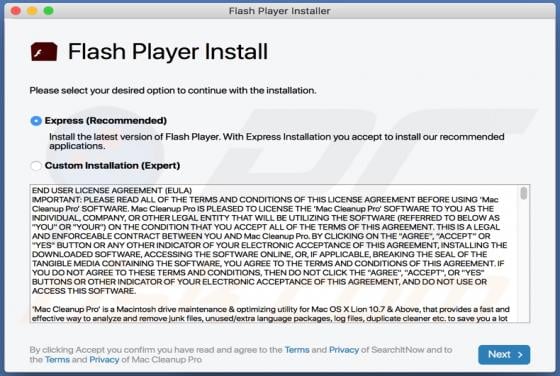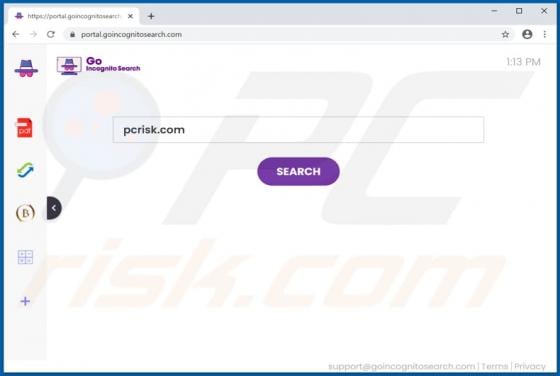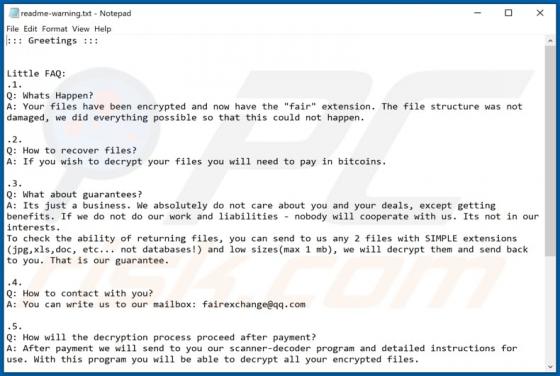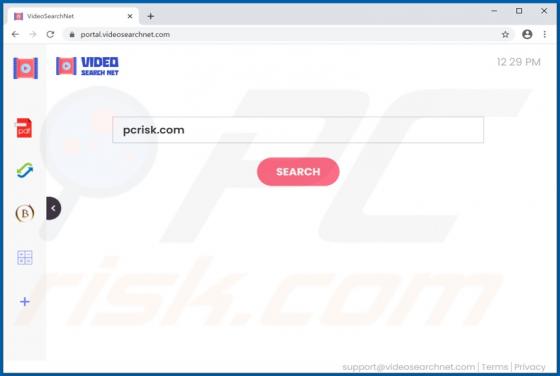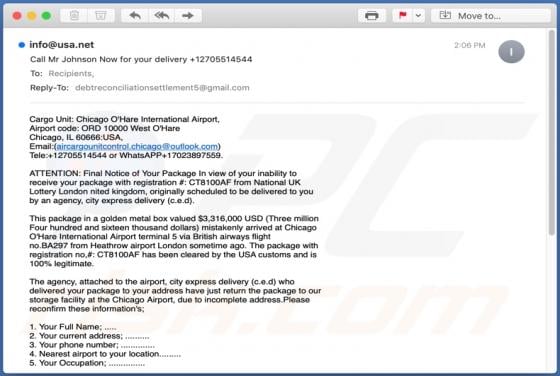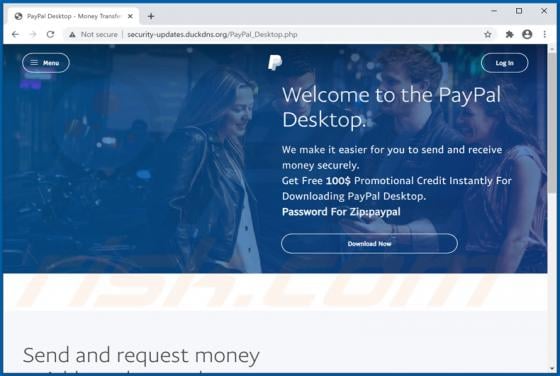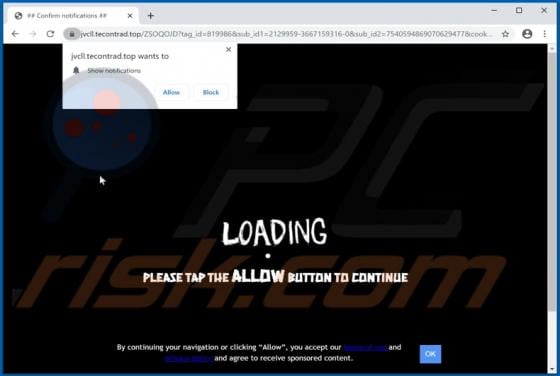
Tecontrad.top Ads
In most cases, websites such as tecontrad[.]top are not visited by users intentionally - they are opened by browsers with potentially unwanted applications (PUAs) installed on them. They are also promoted via dubious advertisements or other bogus web pages. Some examples of web pages similar to t