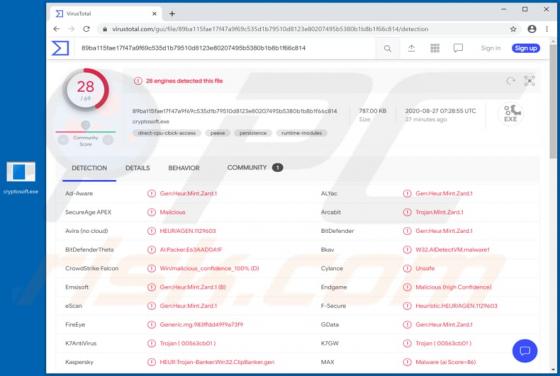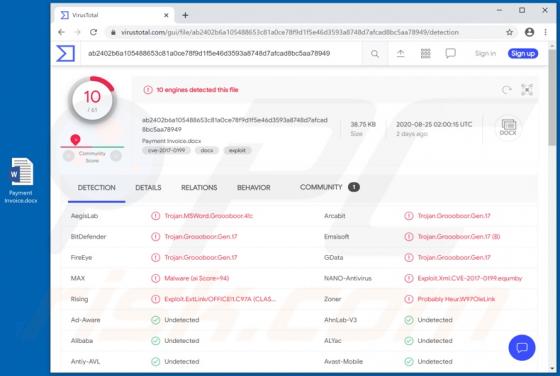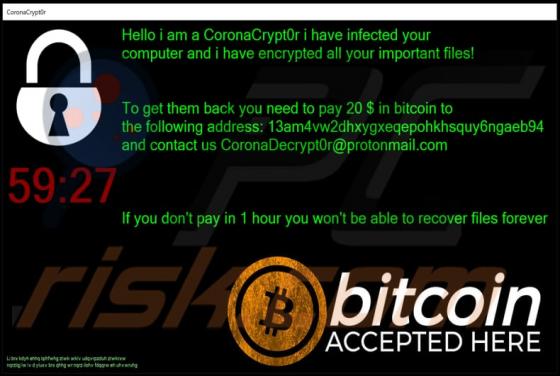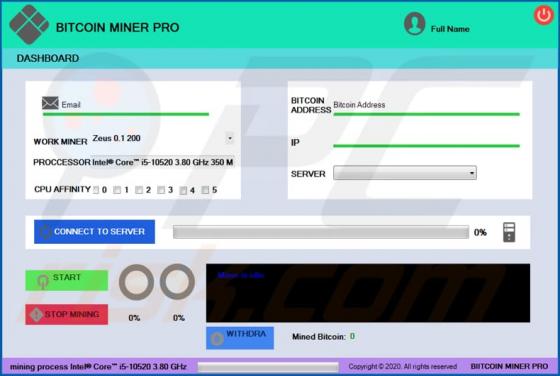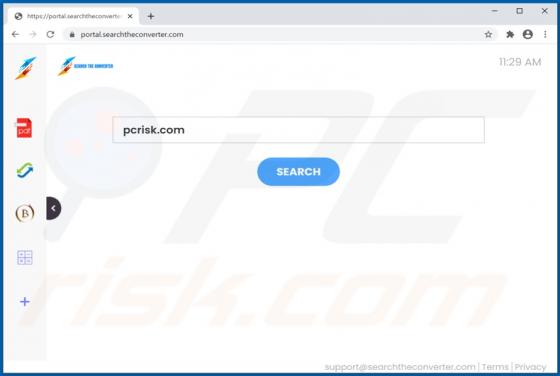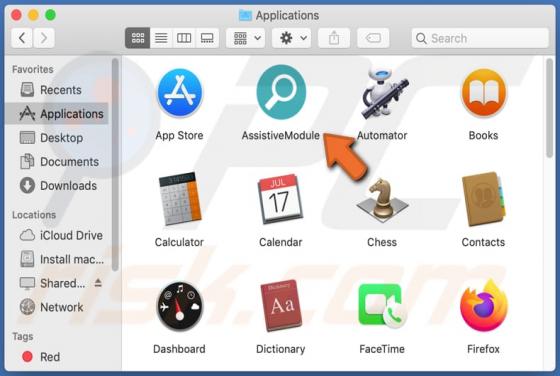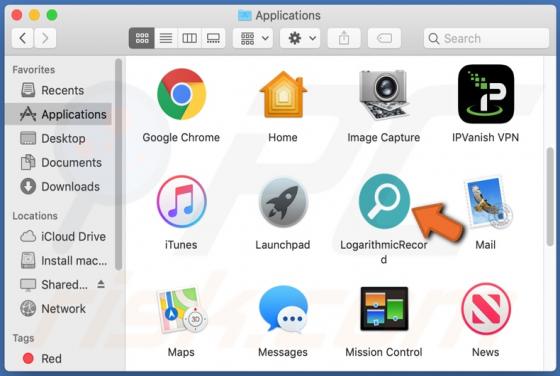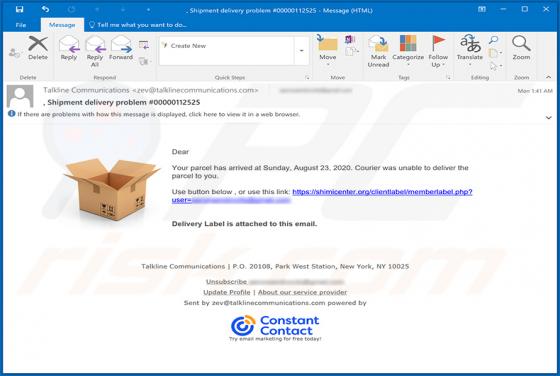
DefaultAnalog Adware (Mac)
DefaultAnalog is an adware-type application with browser hijacker traits. Following successful installation, it delivers intrusive advertisement campaigns, modifies browser settings and promotes fake search engines. On Safari browsers, this app promotes 0yrvtrh.com, whilst on Google Chrome, sear