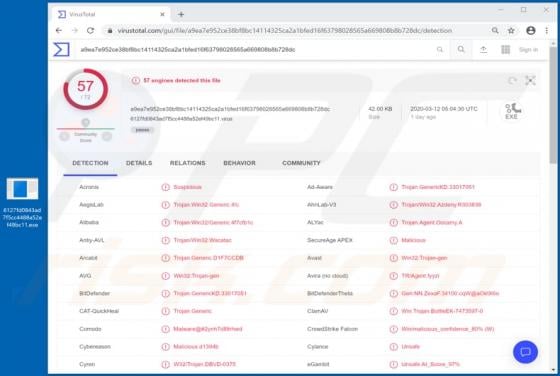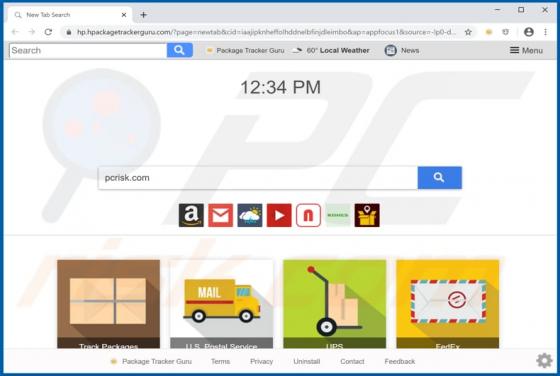
Package Tracker Guru Browser Hijacker
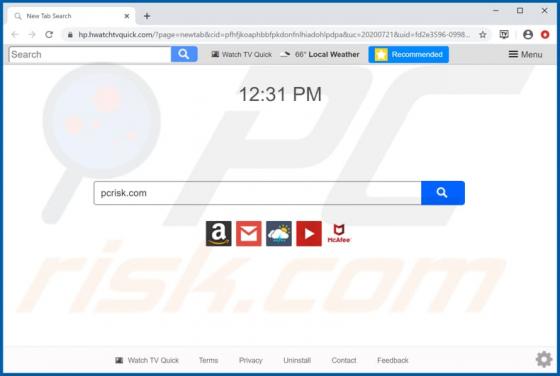
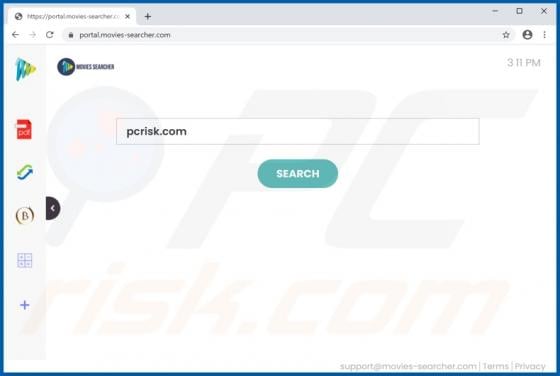
Package Tracker Guru is a typical browser hijacker: it changes certain browser settings to the address of a fake search engine. In this case, it promotes the hpackagetrackerguru.com address. Note that apps of this type can gather browsing data and other information. Users who install Package Trac