Eadytherlayr.club Ads
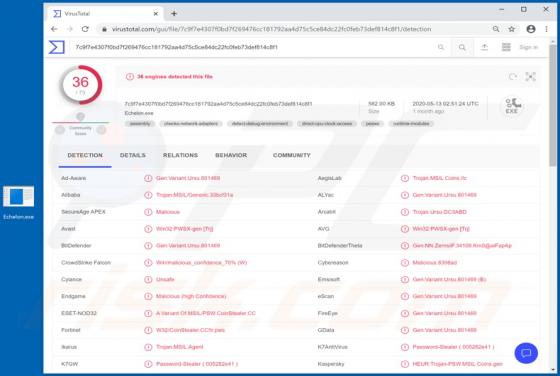
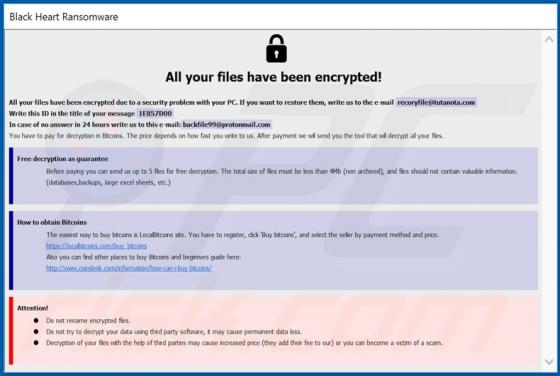
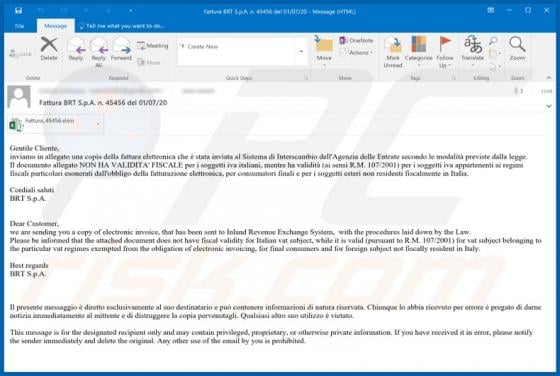
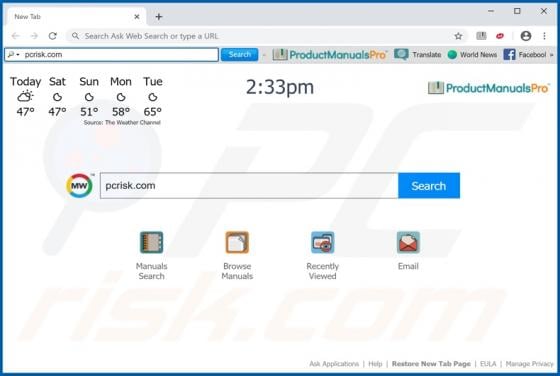
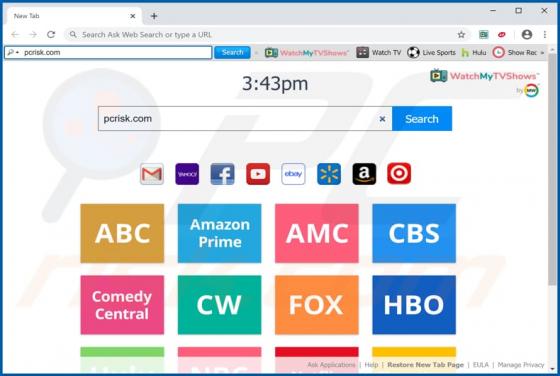
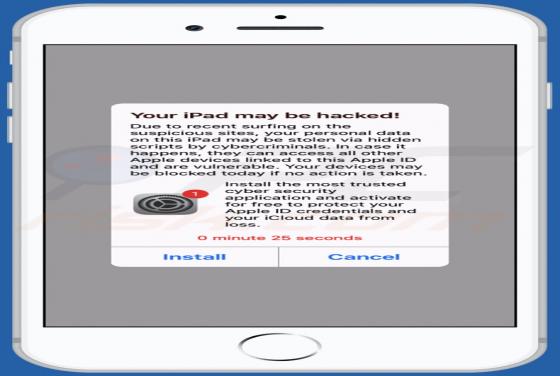
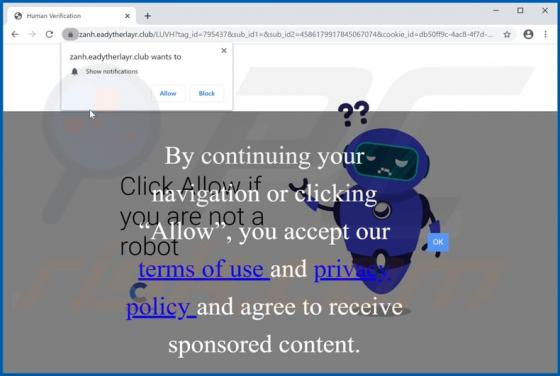
When visited, eadytherlayr[.]club displays dubious content or opens a number of other untrusted websites. There are many pages similar to eadytherlayr[.]club including, for example, mediamodern[.]biz, keysdigita[.]com and zmusic-online[.]com. Commonly, such addresses are opened by installed poten