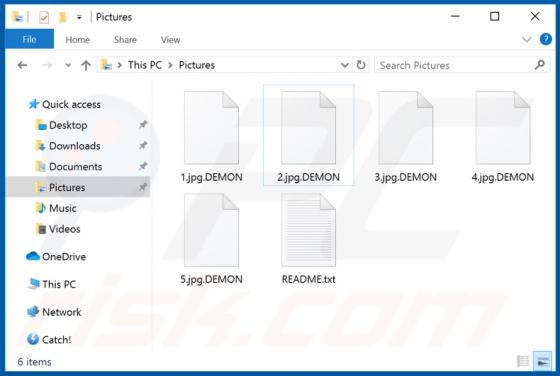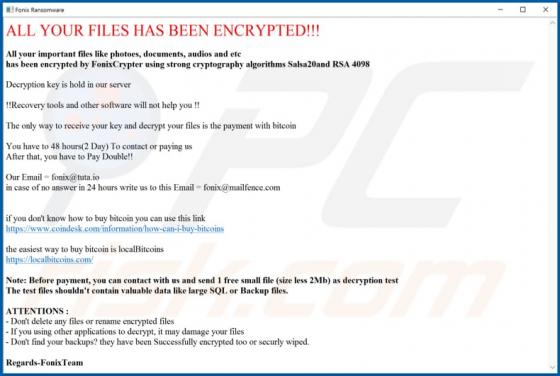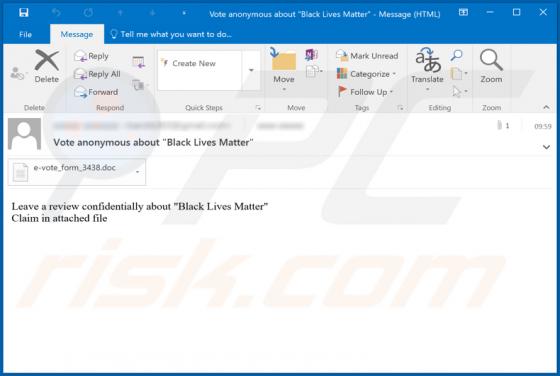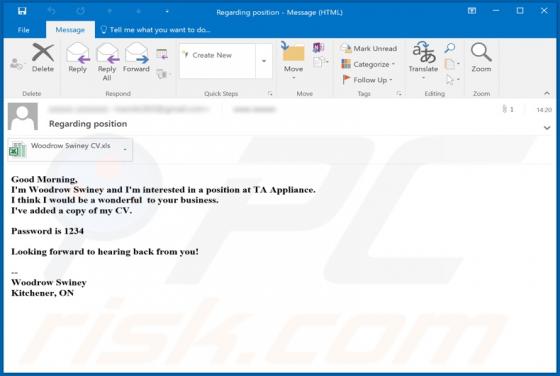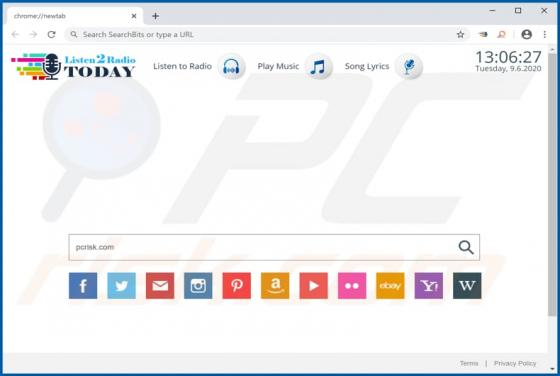
ListenToRadio Browser Hijacker
As its name suggests, ListenToRadio supposedly provides quick access to radio stations and music websites. In fact, the main purpose of this browser hijacker is to promote blpsearch.com (a fake search engine) by changing certain browser settings. Typically, apps of this type modify settings and co