Your Local Network Has Been Compromised Email Scam
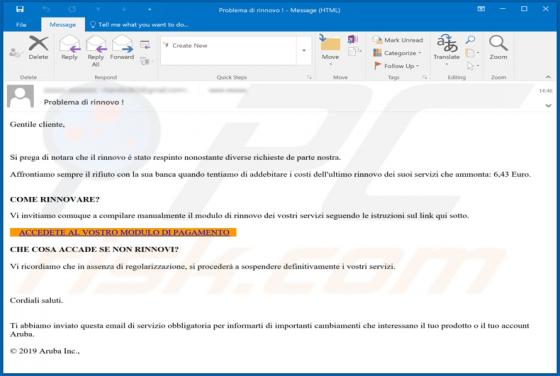
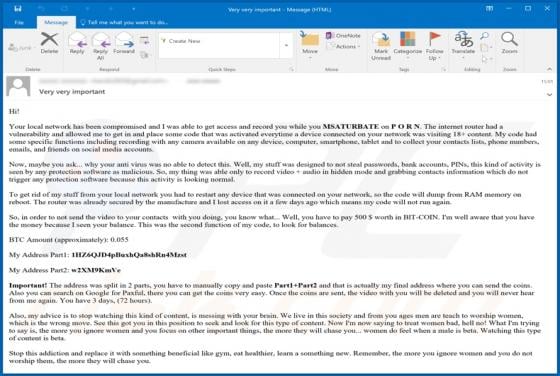
"Your local network has been compromised" is a deceptive email, using the sextortion scam model. The message claims that recipients' devices have been infected with spyware, which has obtained compromising content when pornography websites were supposedly visited. These alleged videos are held fo