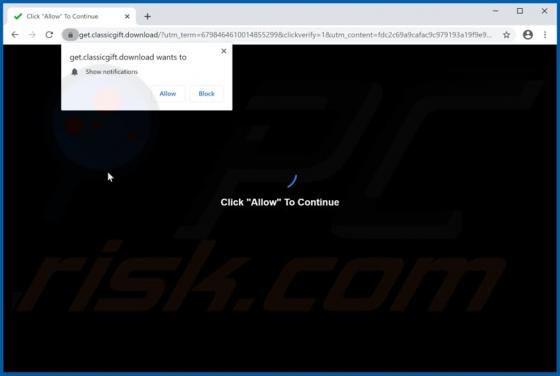
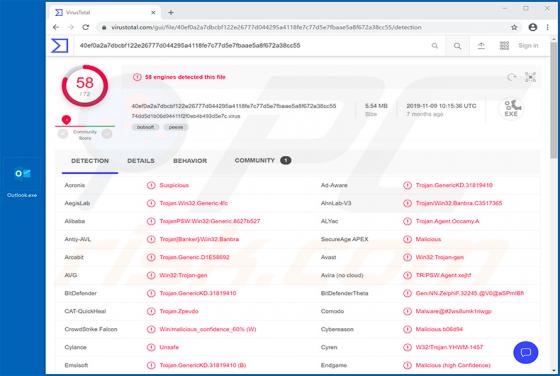
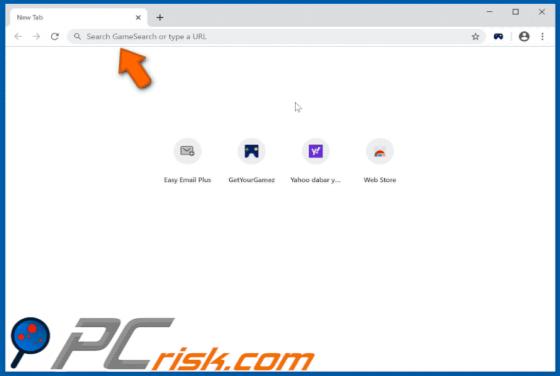
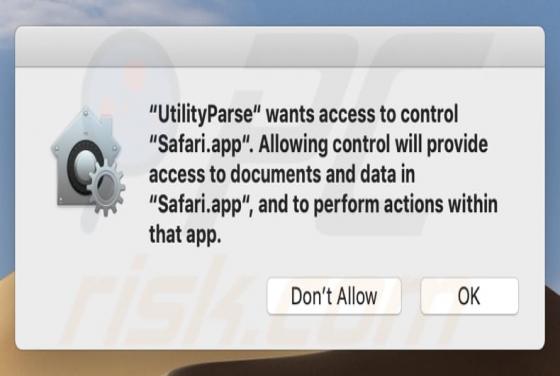
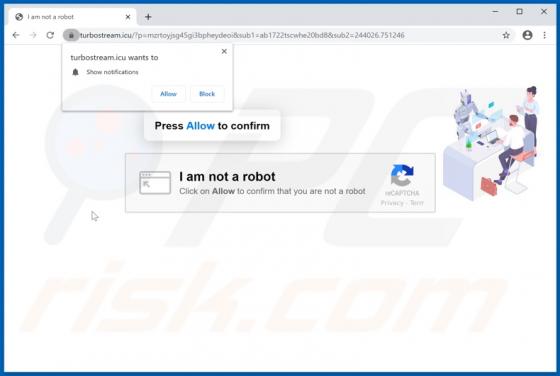
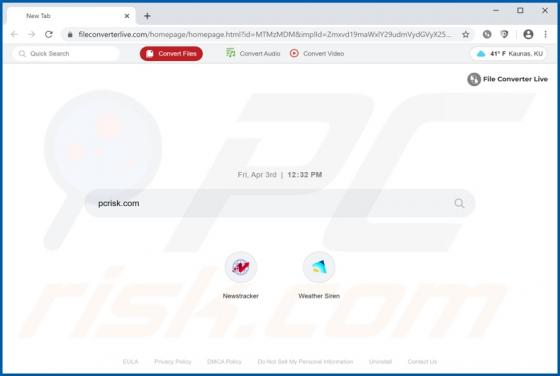
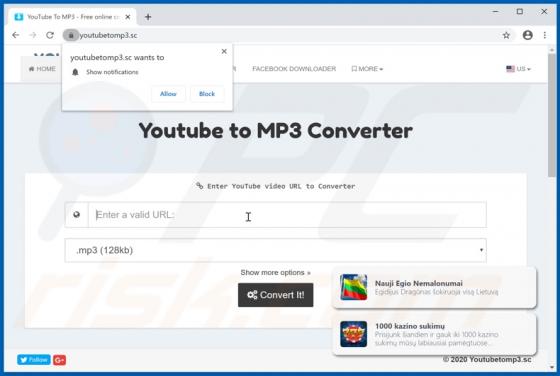
My Social Tab Browser Hijacker
My Social Tab reassigns certain browser settings to hmysocialtab.net. This app is a browser hijacker designed to promote a fake search engine. Apps of this type also gather browsing-related data. Since users often download and install browser hijackers unintentionally, they are categorized as pot