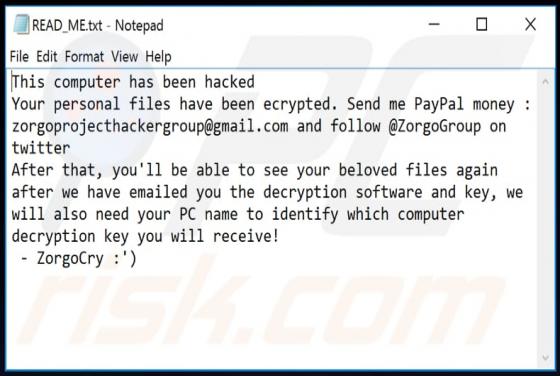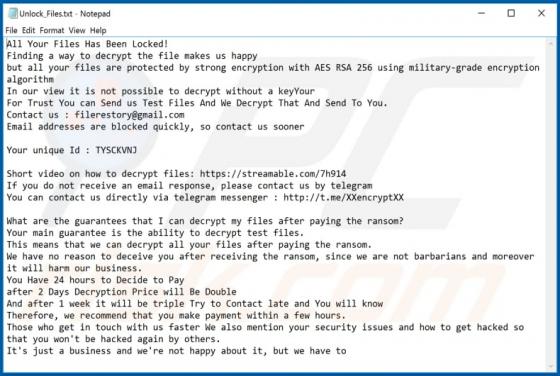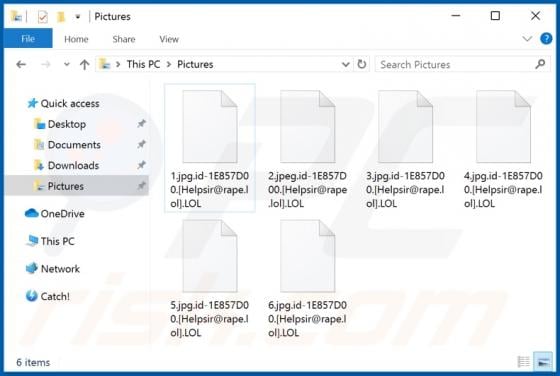
Manuals Aid Browser Hijacker
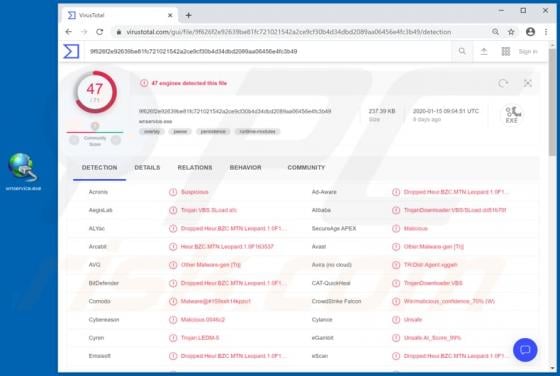
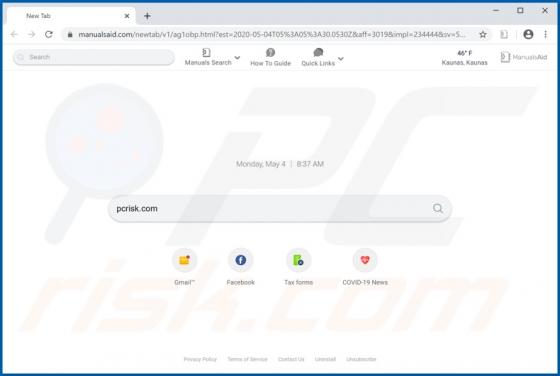
Manuals Aid is rogue software categorized as a browser hijacker. It is endorsed as a tool for easy access to various product and brand manuals, however, Manuals Aid modifies browsers and promotes manualsaid.com (a bogus search engine). Additionally, this browser hijacker has data tracking capabil