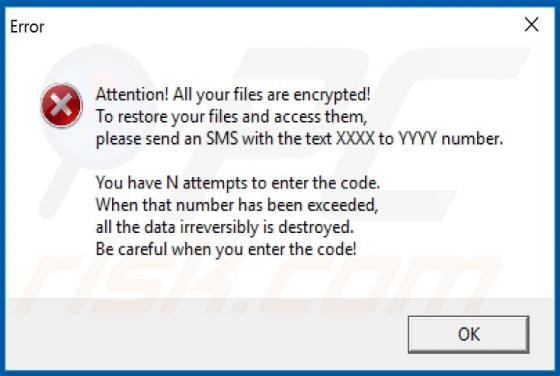
Koti Ransomware
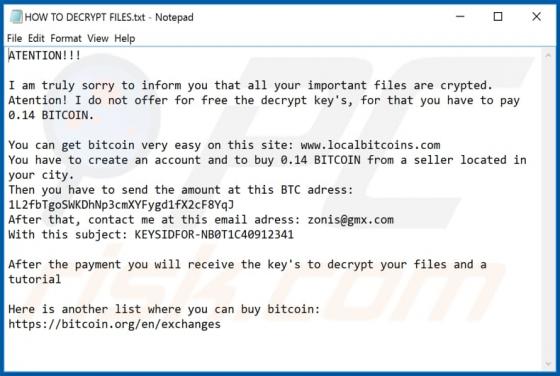
Koti is malicious software, which is part of the Djvu ransomware family. It is designed to encrypt the files of infected systems in order to make ransom demands. When this ransomware encrypts, all affected files are appended with the ".koti" extension. For example, a file originally named somethin