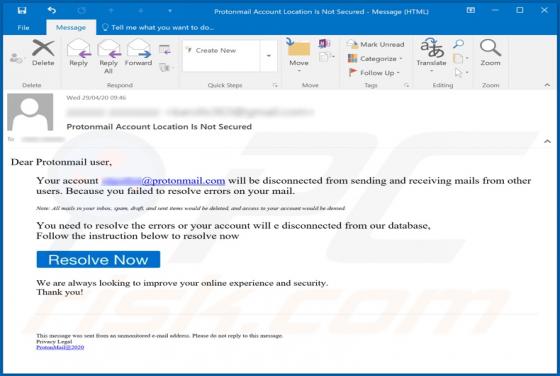
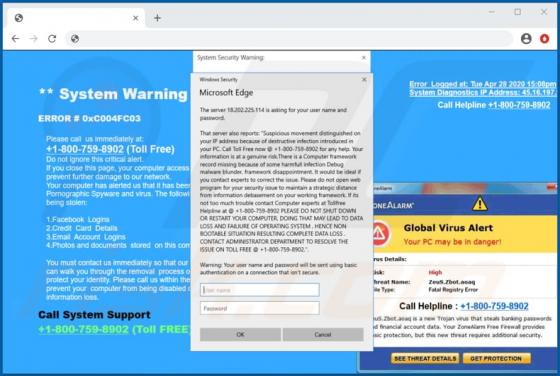
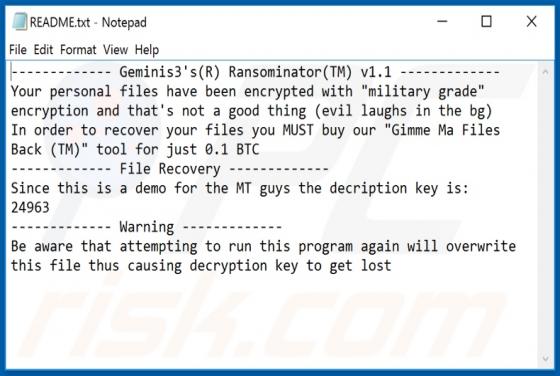
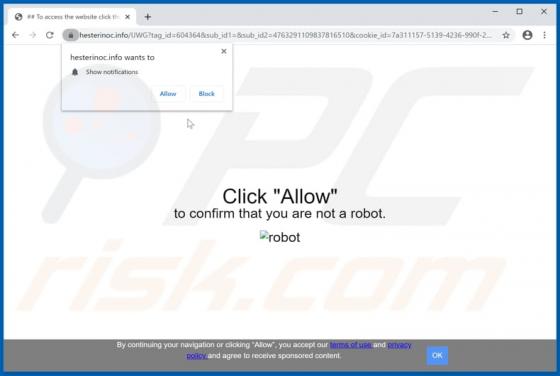
MyGamesSearches Browser Hijacker
MyGamesSearches is a browser hijacker, but advertised as a tool for easy access to various online games. It modifies browser settings and promotes gamsrch.com (a fake search engine). MyGamesSearches also monitors users' browsing habits. Since many people install this software unintentionally, it i