InteractiveSpeed Adware (Mac)
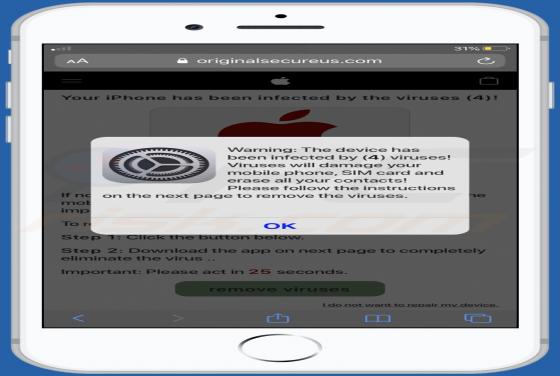
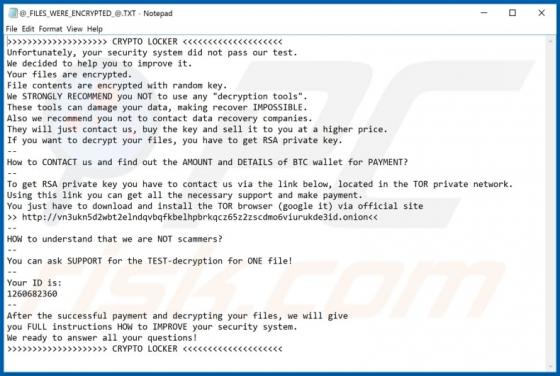
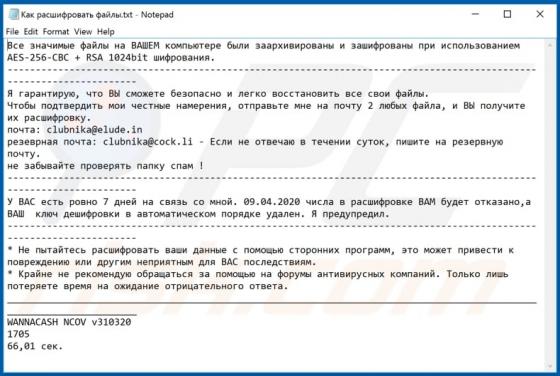
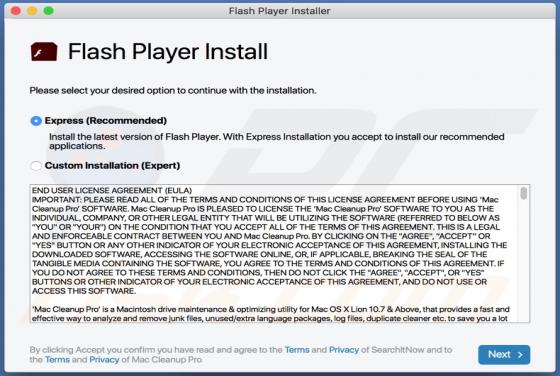
InteractiveSpeed serves advertisements, collects various information (including sensitive data) and promotes Safe Finder via akamaihd.net. This app is classified as a potentially unwanted application (PUA) and adware. Typically, people download and install apps of this type inadvertently.