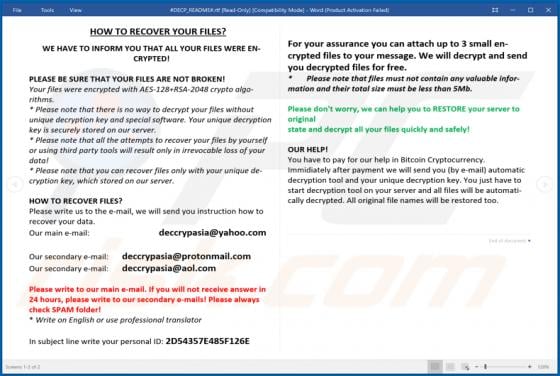
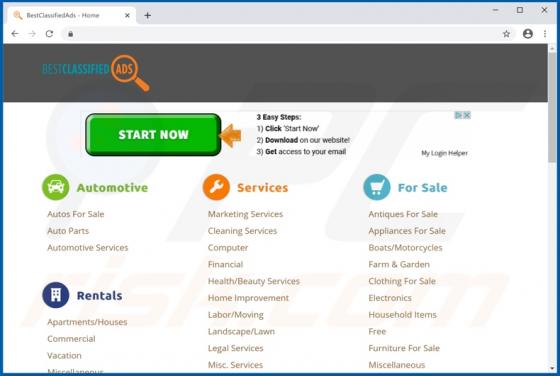
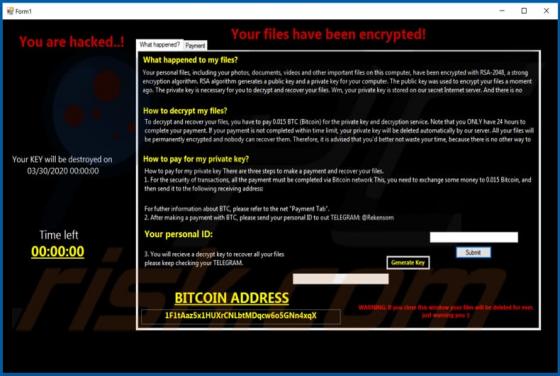
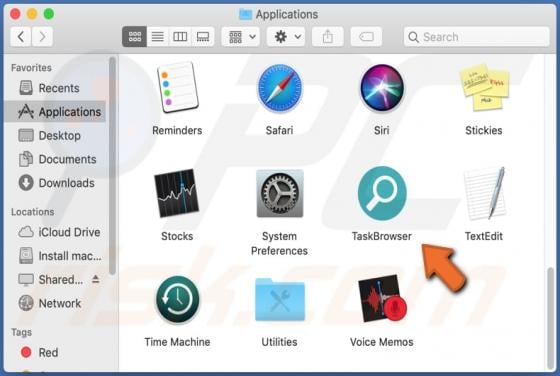
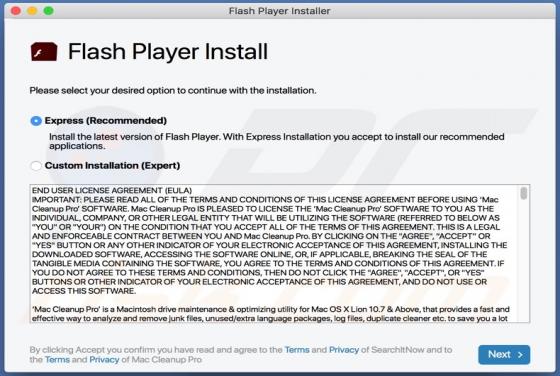
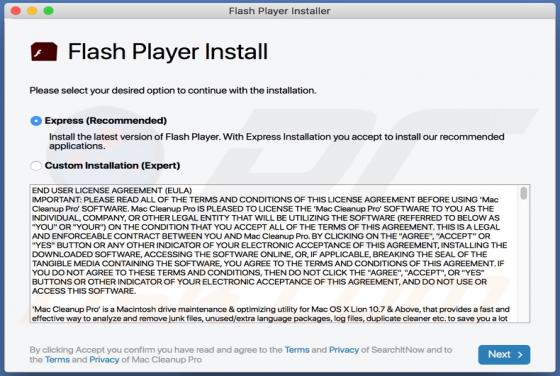
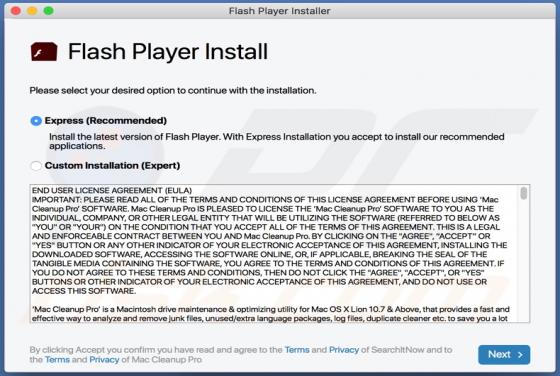
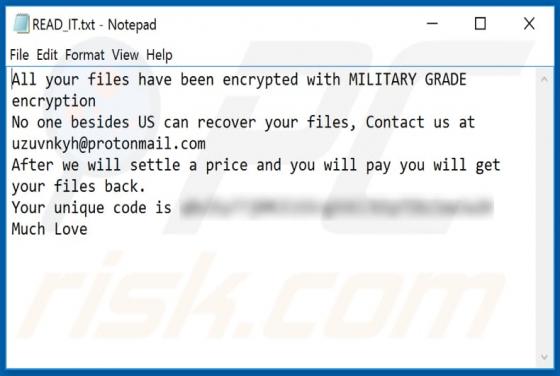
Booster Search Browser Hijacker
Booster Search (also known as BoosterSearch) is an application designed to improve the browsing experience. In fact, this is a browser hijacker which promotes feed.boostersearch.com (the address of a fake search engine) by modifying browser settings and gathering various information. In most case