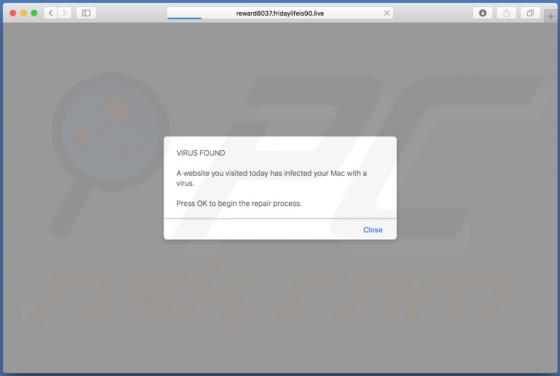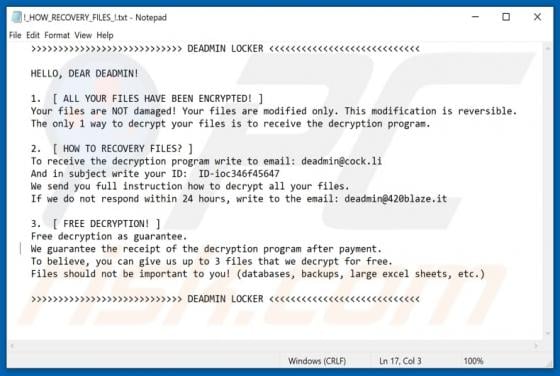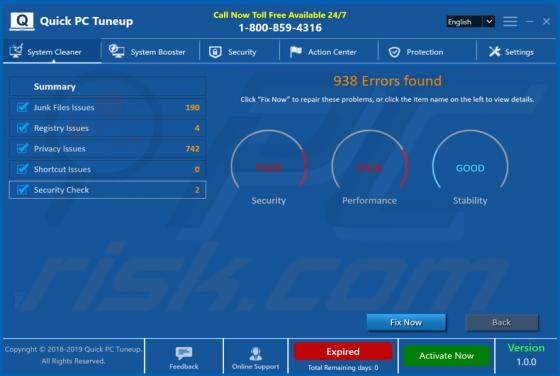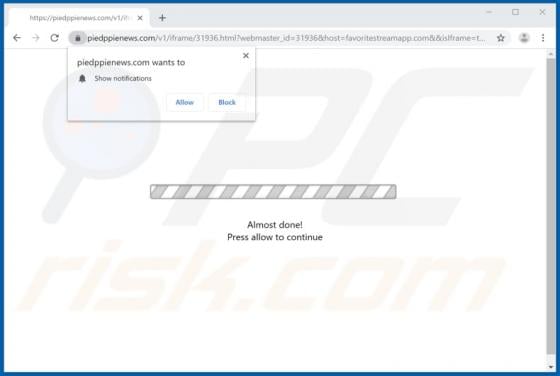
Happy.goodluckspace.com POP-UP Scam (Mac)
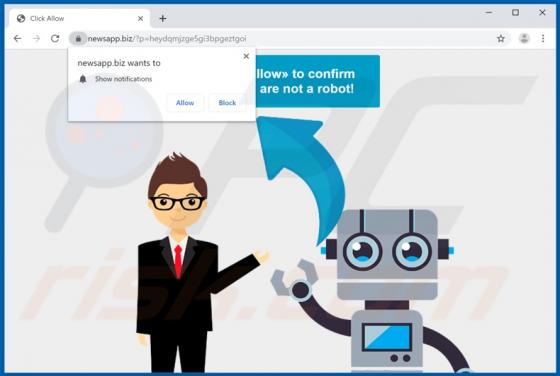
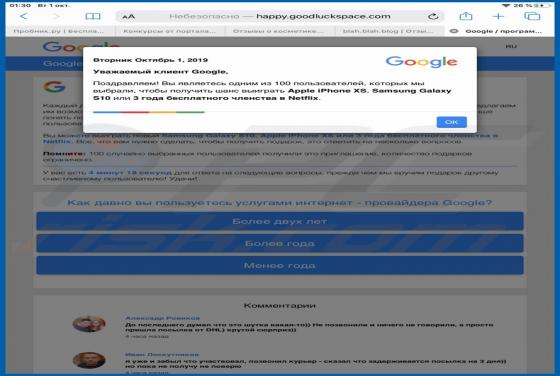
happy.goodluckspace[.]com is one of many dubious websites claiming that the visitor has a chance to win a prize. To participate in the lottery, the visitor is asked to complete a survey and answer various questions. Websites such as happy.goodluckspace[.].com often ask to provide various details