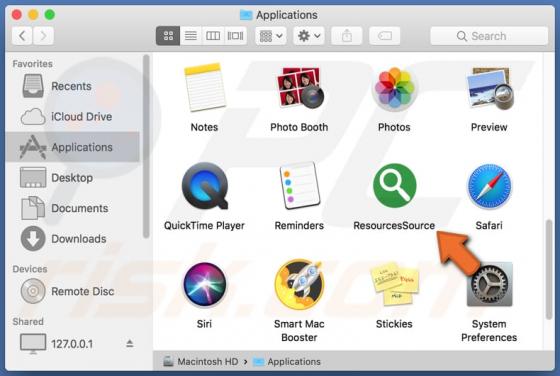
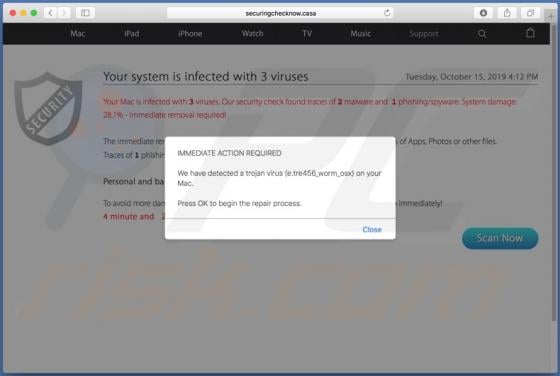
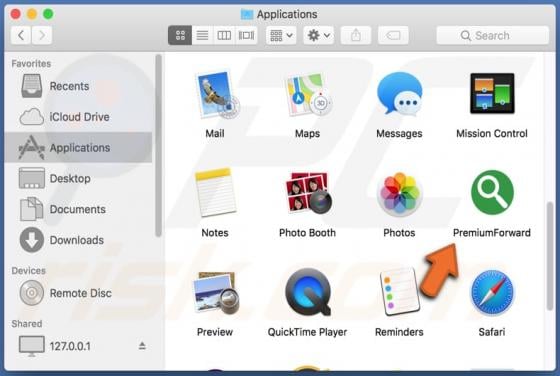
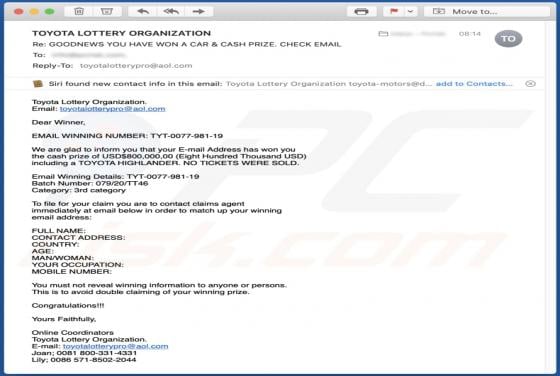
PdfProDocs Browser Hijacker
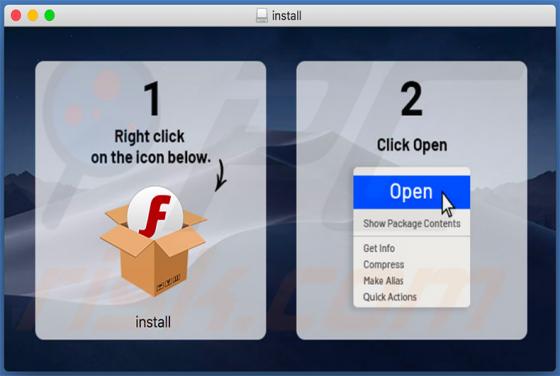
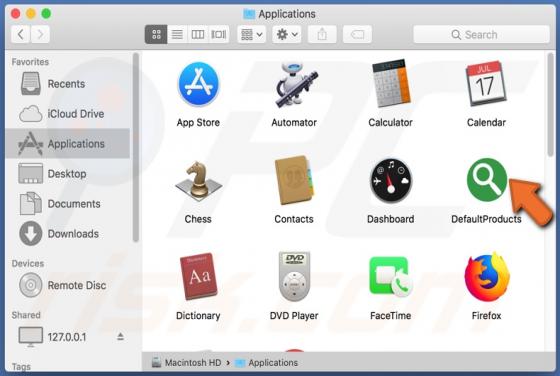
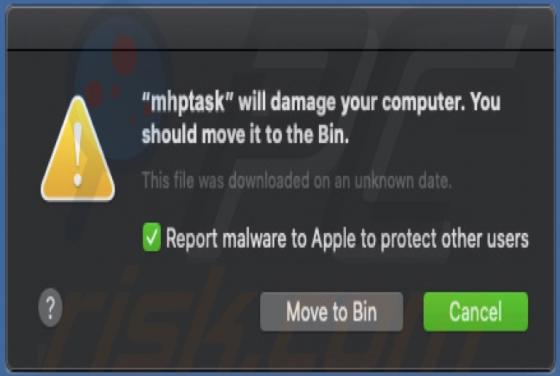
PdfProDocs is a rogue application promoted as a PDF file converter and supposedly capable of converting any file into the PDF format. In fact, it operates as a browser hijacker and makes unauthorized changes to browser settings to promote pdfprodocs.com, a fake search engine. Furthermore, PdfProD