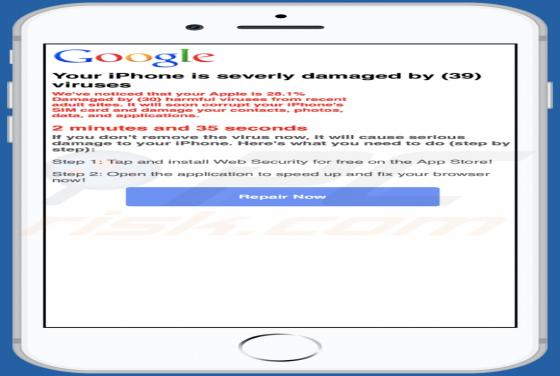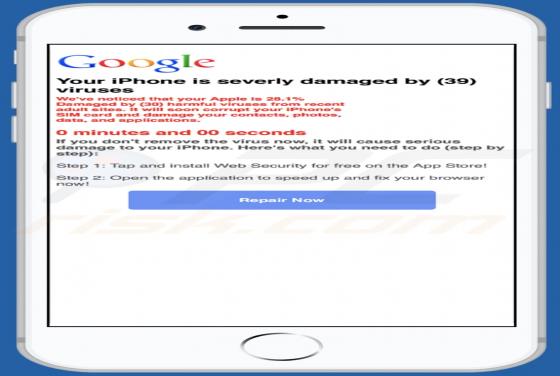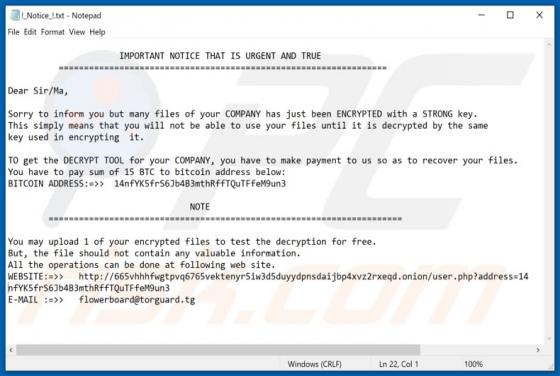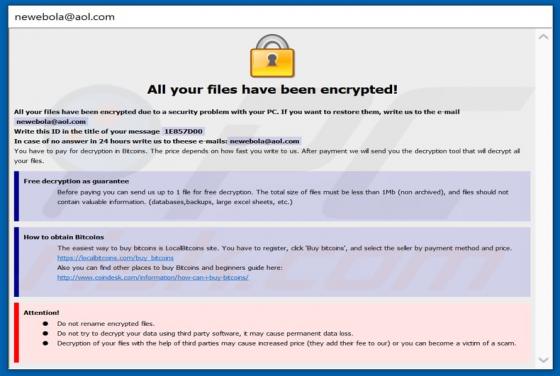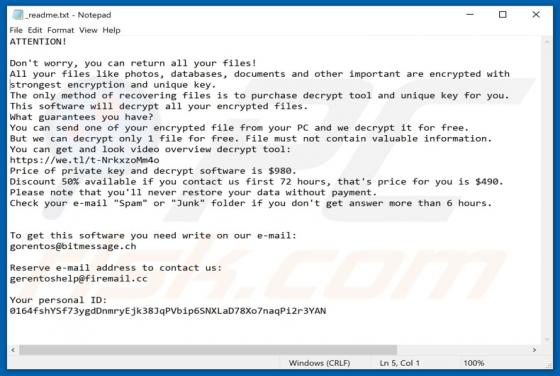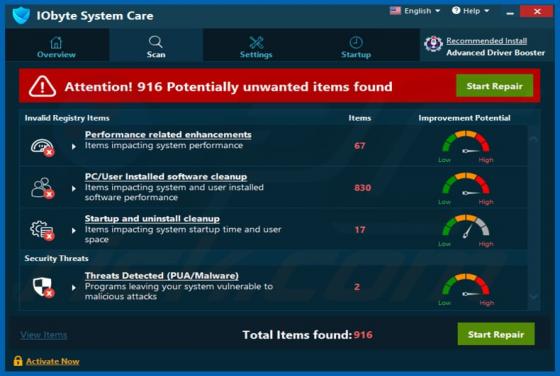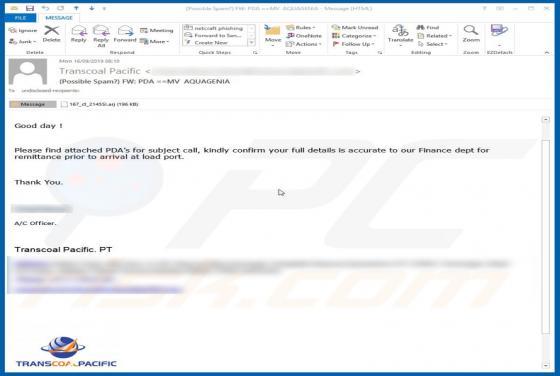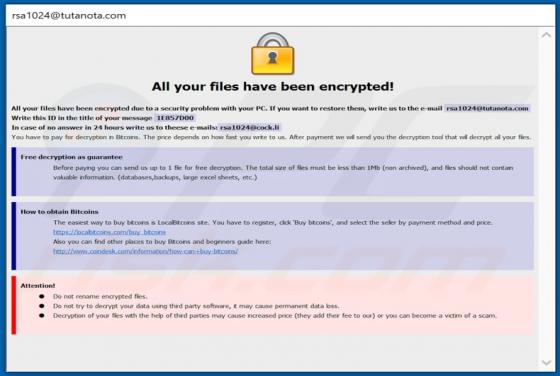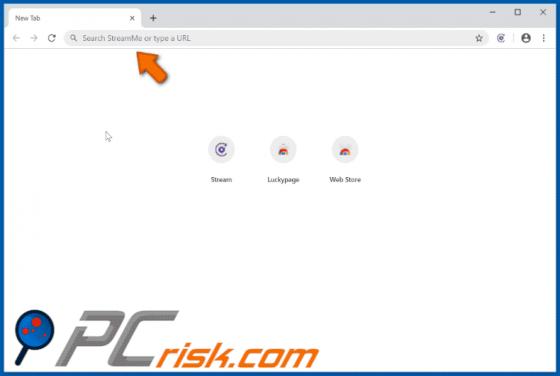
Feed.stream-me.com Redirect
StreamMe is endorsed as a tool for easy access to newest TV related content with an enhanced web search. While seemingly useful and innocuous, StreamMe is a browser hijacker. It modifies browser settings to promote its fake search engine (feed.stream-me.com) and spies on users' browsing habits. I