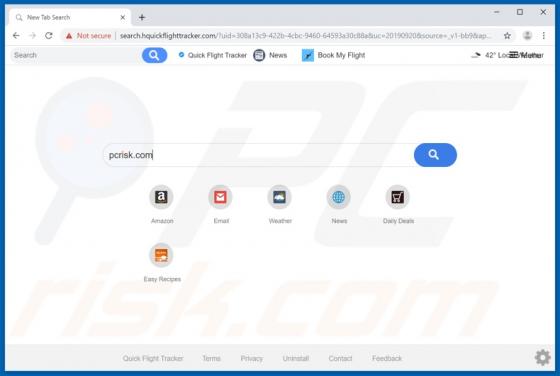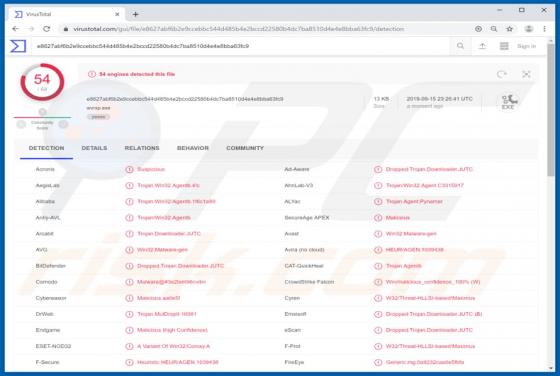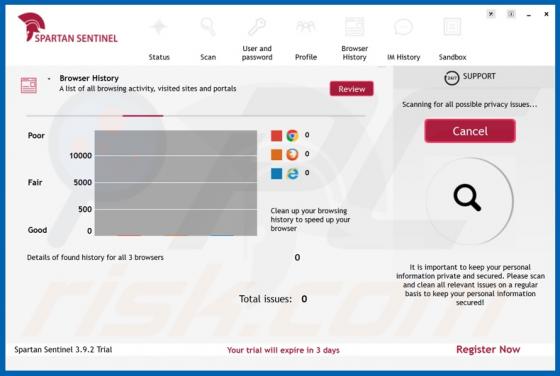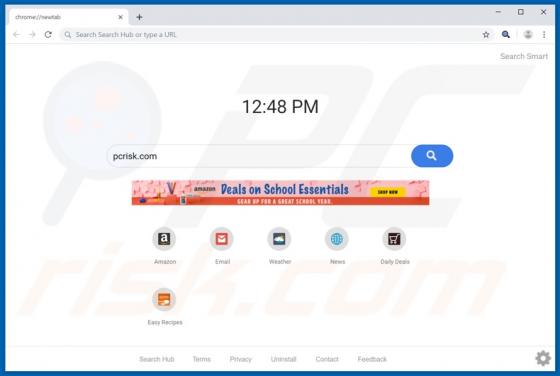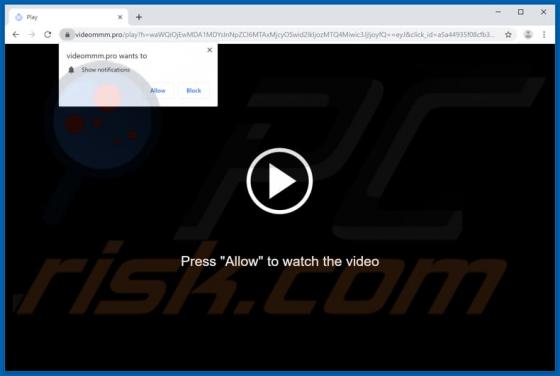
Videommm.pro Ads
videommm[.]pro is a dubious website. If opened, it forces people to visit other untrustworthy websites or displays dubious content. There are many websites similar to videommm[.]pro. Other examples are mediasvideo[.]world, cudalbapt[.]com, and celeb-secret[.]live. People rarely open these sites i