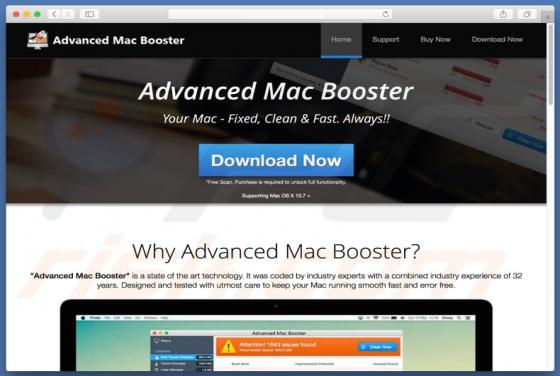
Advanced Mac Booster Unwanted Application (Mac)
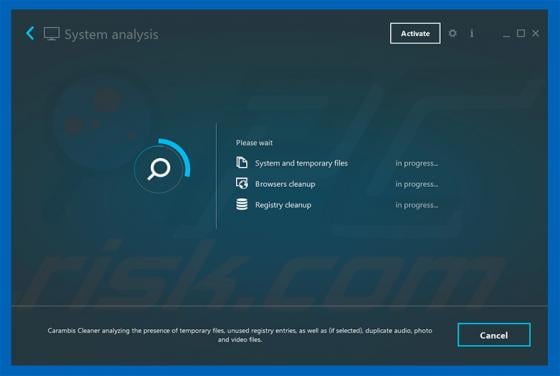
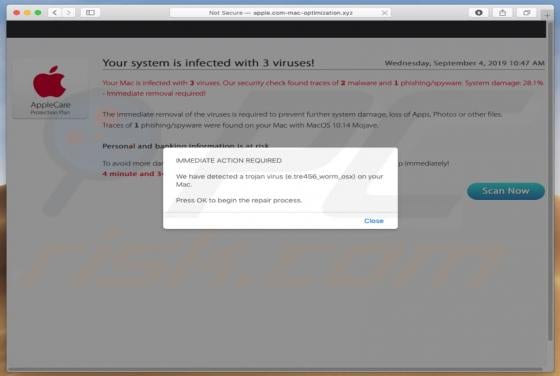
Developers of Advanced Mac Booster application state that this app optimizes MacOS systems. It supposedly allows users to clean MacOS systems, fix various issues, thus improving overall operating system performance. In fact, this app is classified as a potentially unwanted application (PUA) and