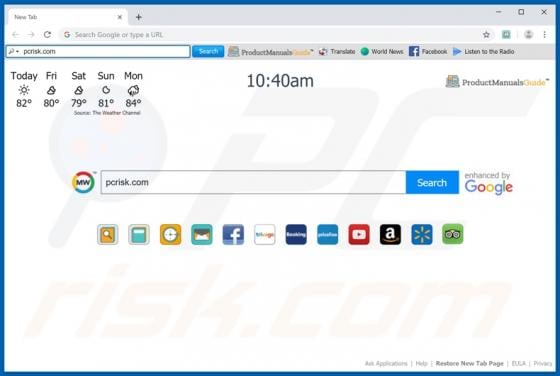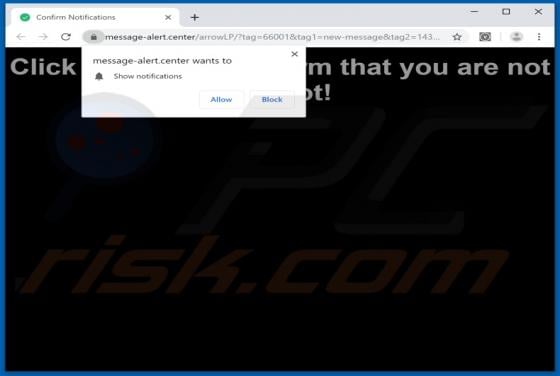
Message-alert.center Ads
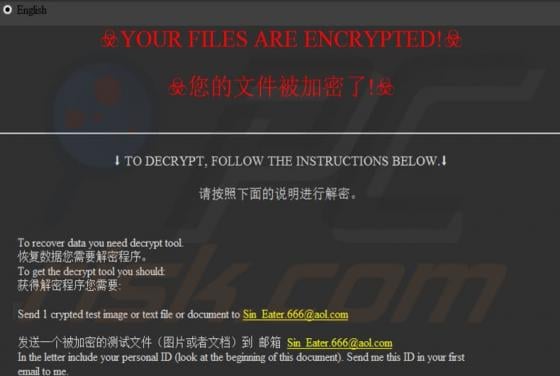
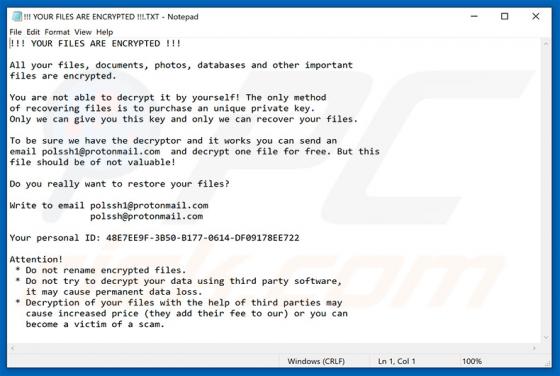
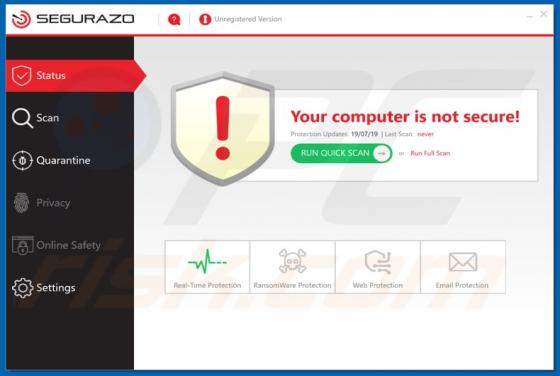
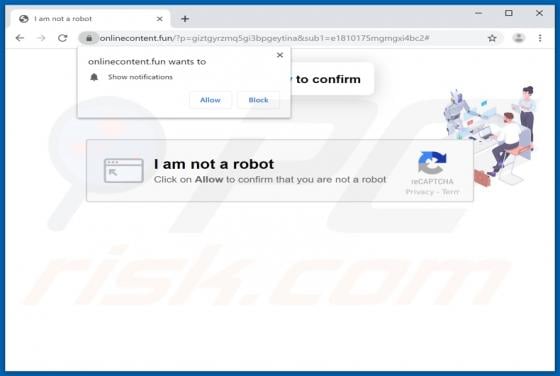
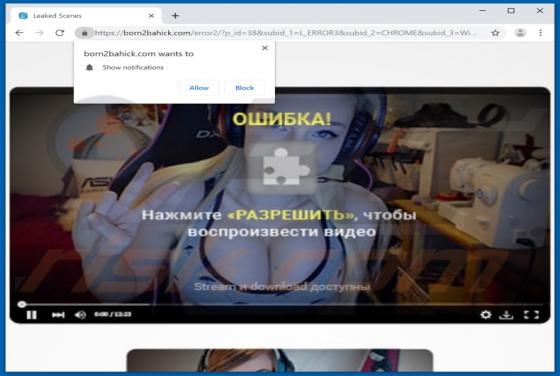
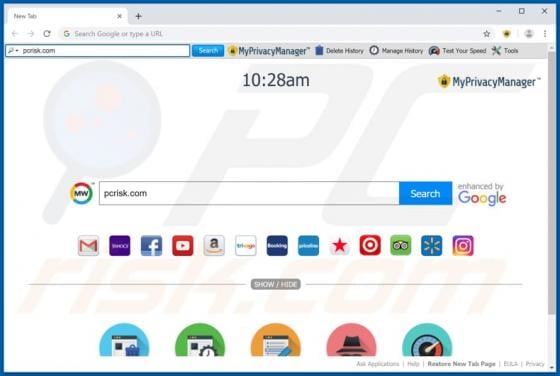
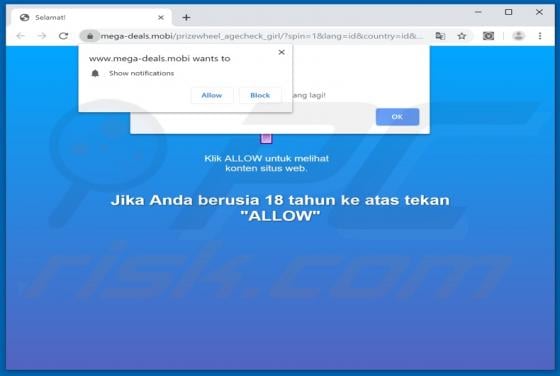
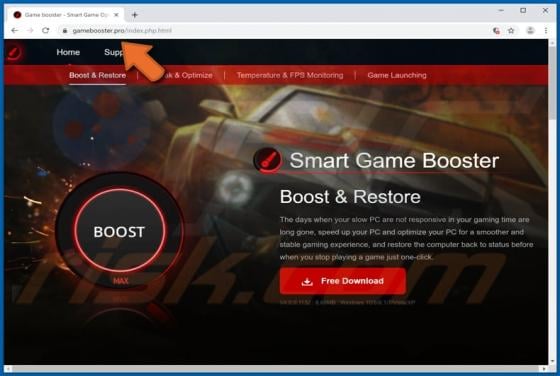
Like thousands of others (e.g. bigclicker.me, dredrewlaha.info, checking-your-browser.com and etc.), message-alert[.]center is a rogue website. Designed to cause rampant redirects to compromised and possibly malicious sites, as well as delivery of highly dubious content. What should be known, is