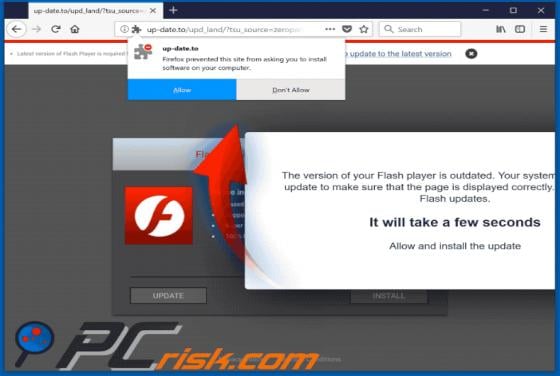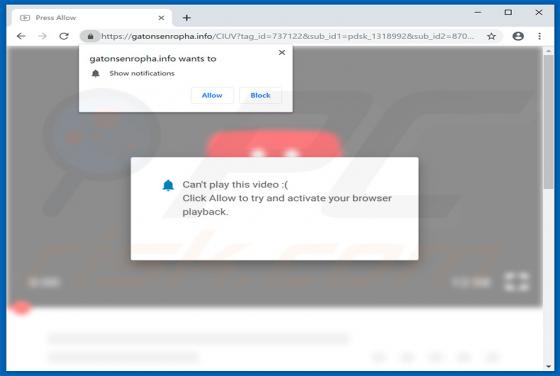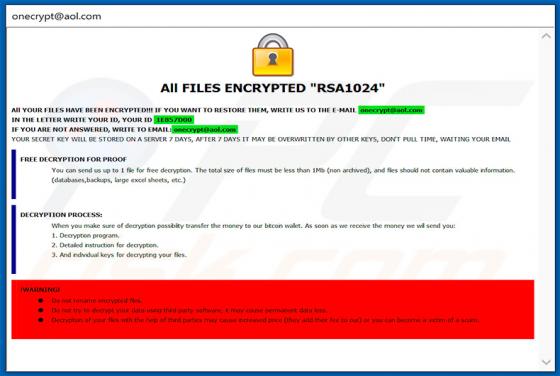
.good (Dharma) Ransomware
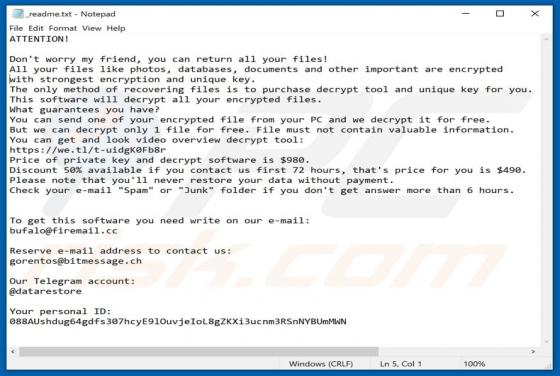
First discovered by malware researcher Jakub Kroustek and belonging to the Dharma ransomware family, .good is high-risk ransomware that stealthily infiltrates computers and encrypts most stored files. This ransomware also appends filenames with the ".good" extension (hence its name) during encrypt