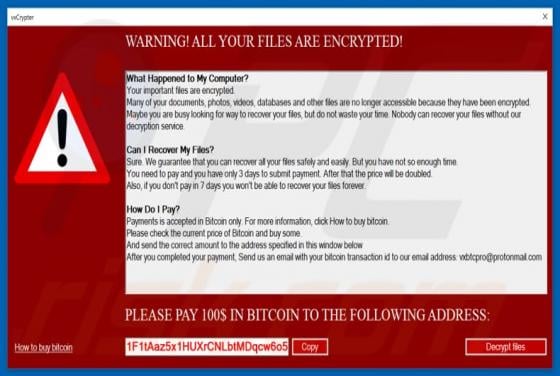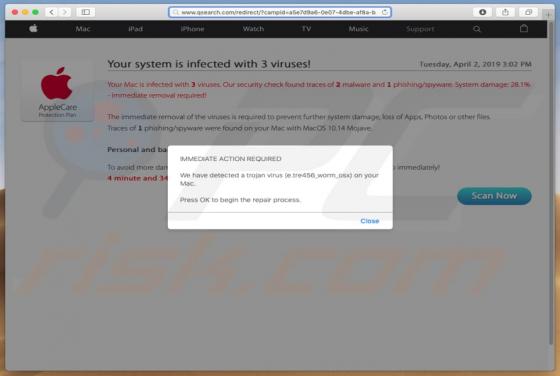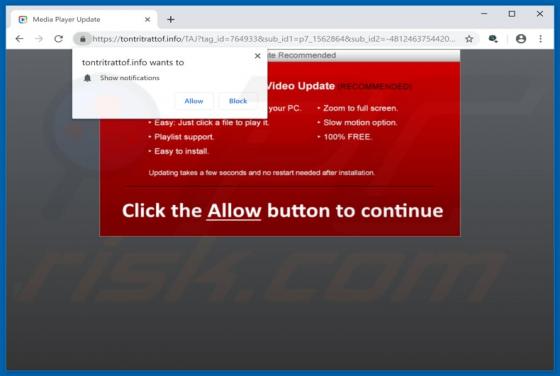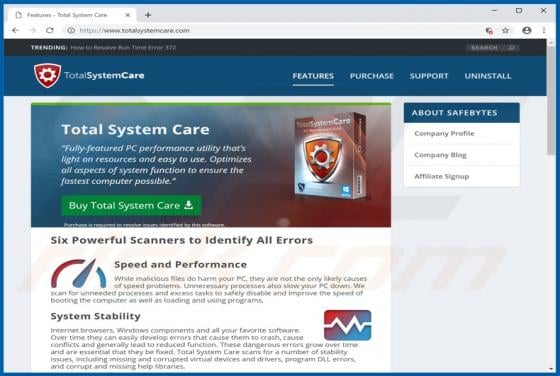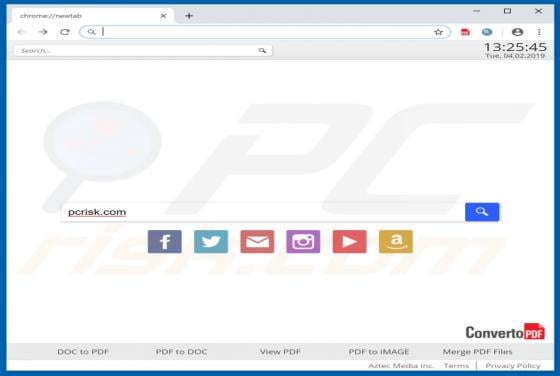
ConvertoPDF Browser Hijacker
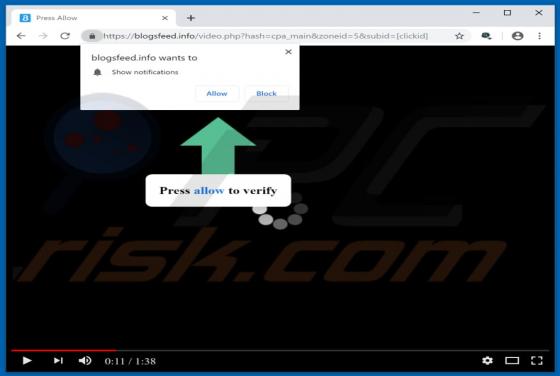
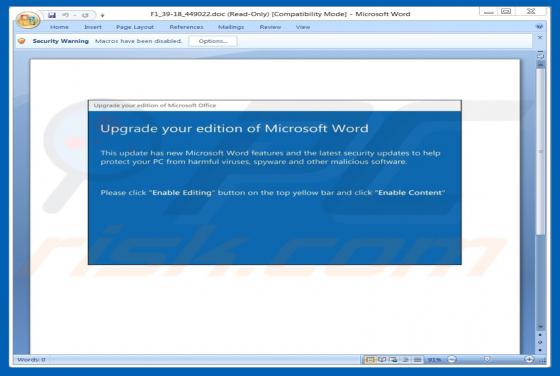
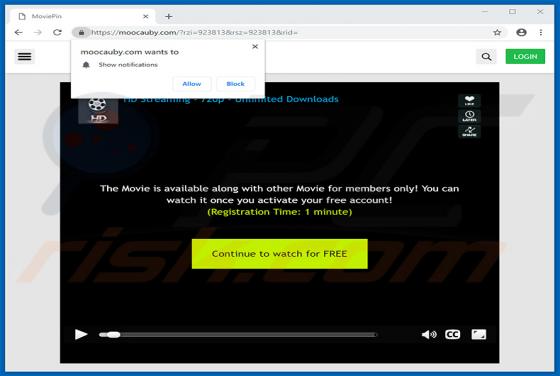
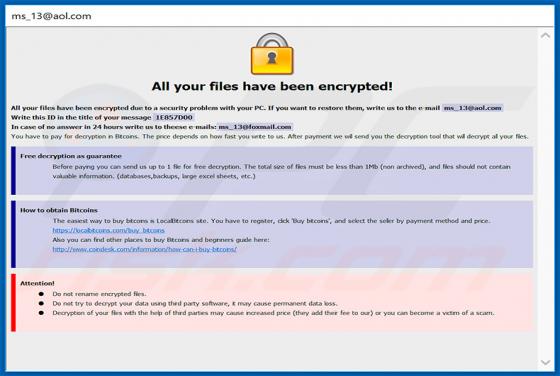
According to the developers, the ConvertoPDF app allows users to quickly convert PDF files directly from their browsers. This may seem to be a useful feature, however, ConvertoPDF is a potentially unwanted application (PUA), a browser hijacker. Generally, people download and install apps of this t