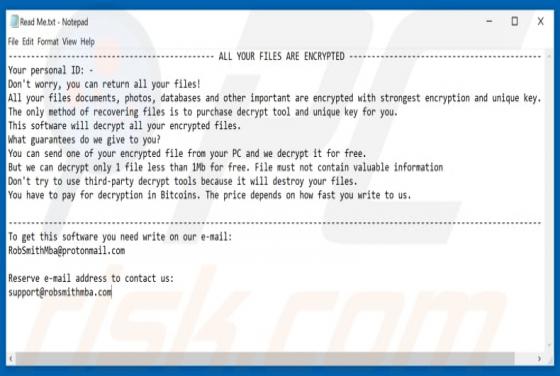
BigBobRoss Ransomware
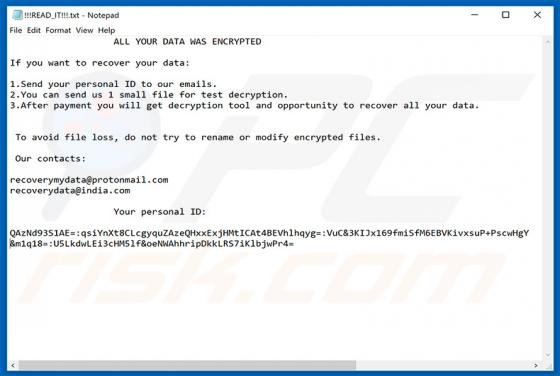
Discovered by Michael Gillespie, BigBobRoss is malicious software categorized as ransomware. As with most programs of this type, it blocks access to victims' data unless ransoms are paid. This is a new variant of Obfuscated ransomware (the previous version was decrypted by Avast, and so cyber crim