MacPro Install Adware (Mac)
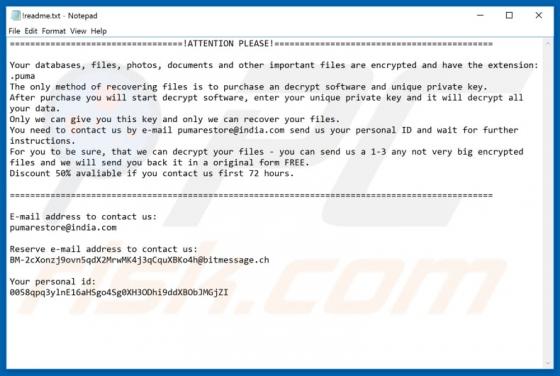
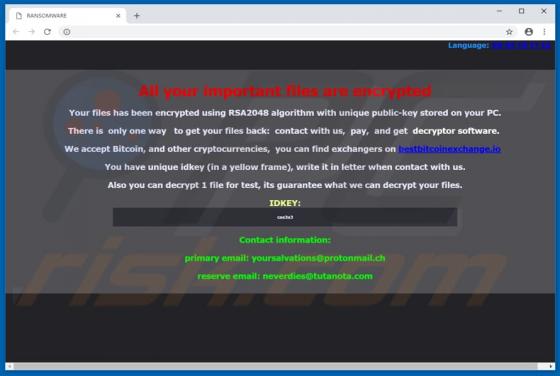
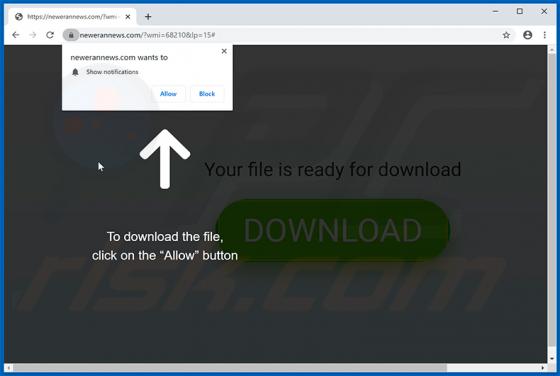
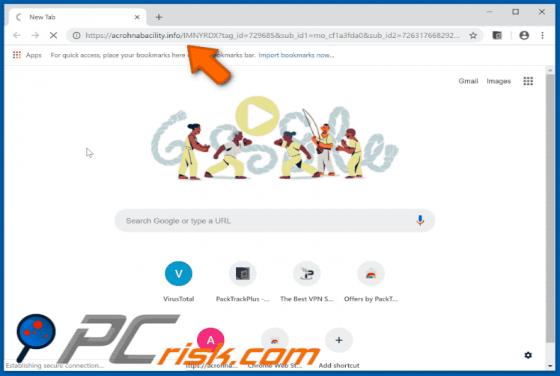
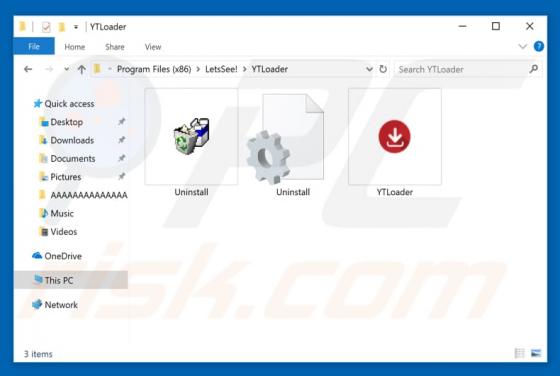
According to the developers, the MacPro Install application supposedly makes the installation and download process easier. This may seem a useful tool, but it is categorized as a potentially unwanted application (PUA) and an adware-type app since most users install it unintentionally. MacPro Ins