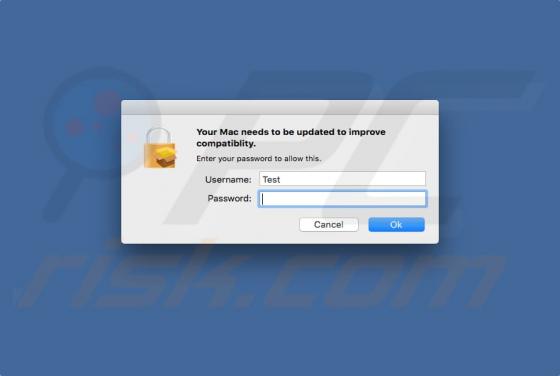
Your Mac Needs To Be Updated To Improve Compatibility POP-UP Virus (Mac)
Similar to "Apple Wants To Make Changes", "Your Mac needs to be updated to improve compatibility" is a pop-up message encouraging Mac users to install updates that will improve computer compatibility. Recently, many users started encountering this pop-up. Be aware, however, that this is a scam a