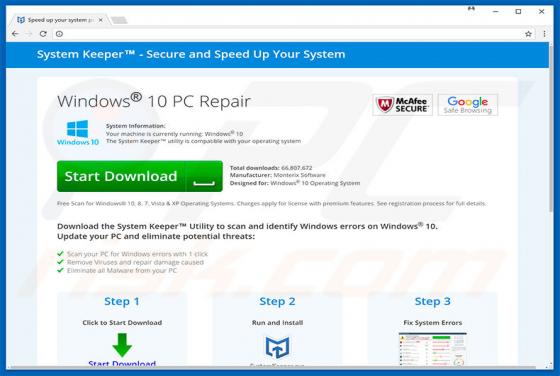
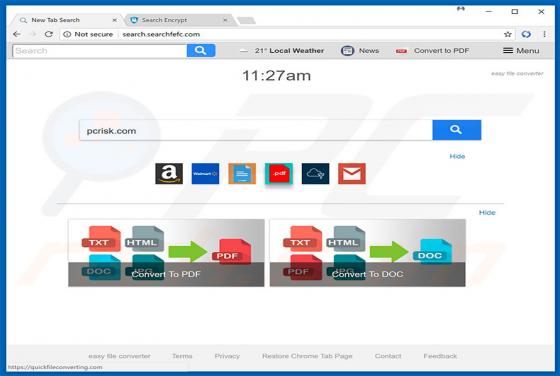
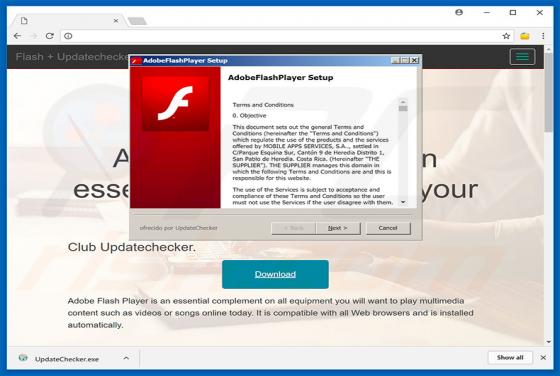
IdleBuddy Virus
IdleBuddy is deceptive crypto-mining software often distributed with various potentially unwanted adware-type programs. Research shows that adware commonly infiltrates systems without consent. Immediately after infiltration, adware-type applications deliver intrusive advertisements and collect inf