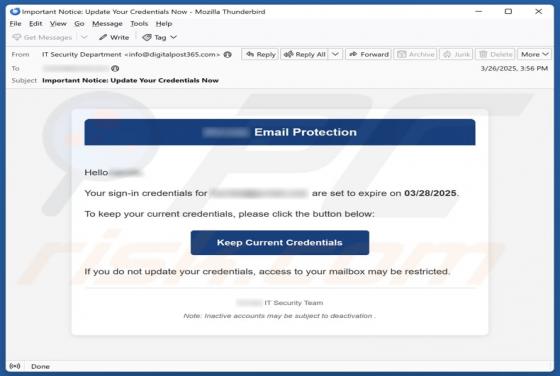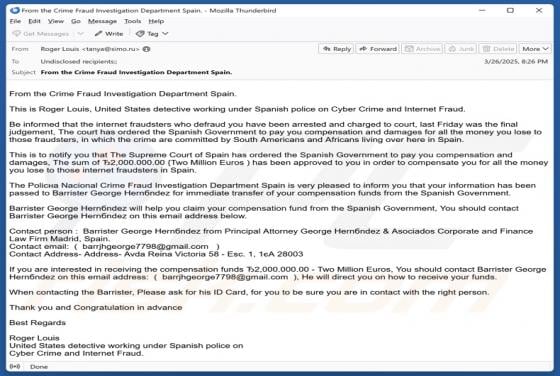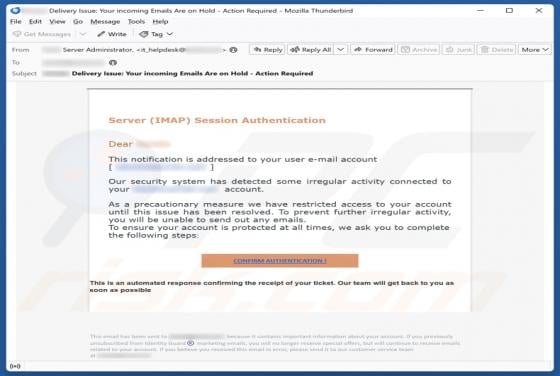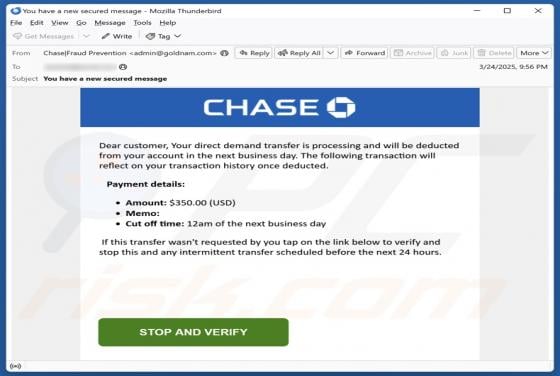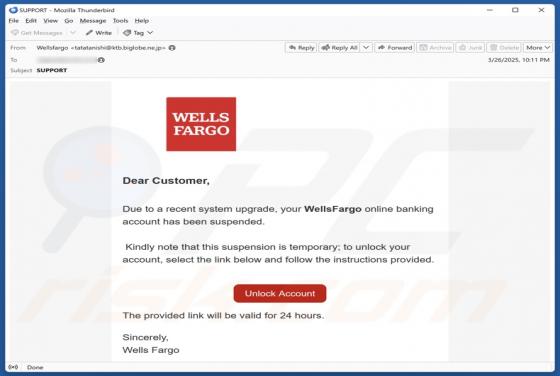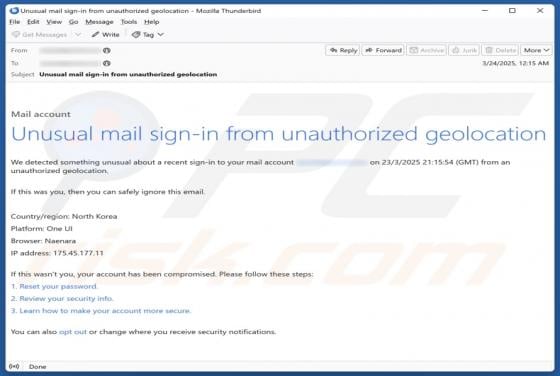
Sign-in From Unauthorized Geolocation Email Scam
Our team has inspected the email and found that this is a phishing email disguised as a notification regarding an unusual sign-in from unauthorized geolocation. It leads to a phishing website designed to pilfer sensitive information from recipients. Such emails should be ignored to avoid potential