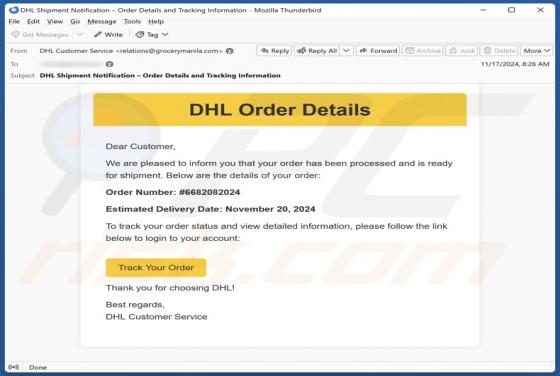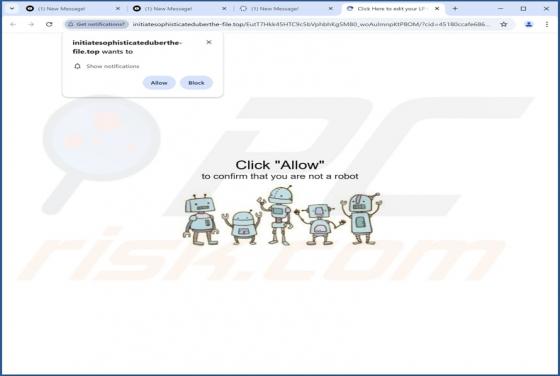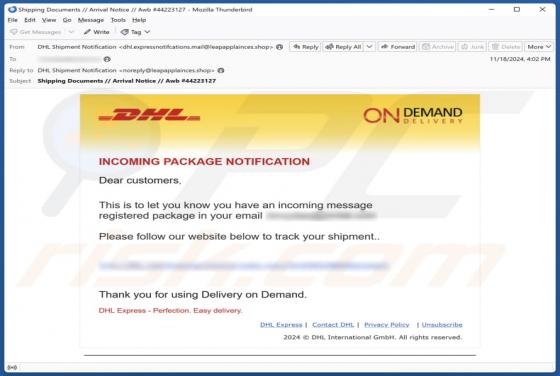
DHL - INCOMING PACKAGE NOTIFICATION Email Scam
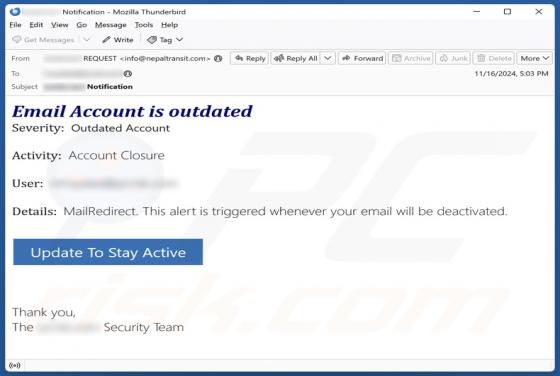
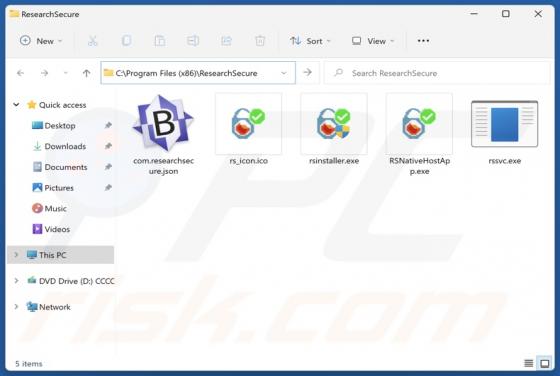
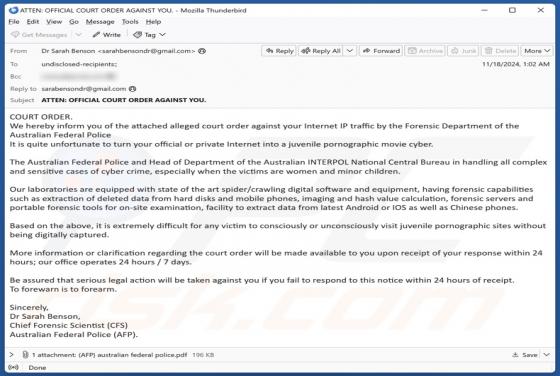
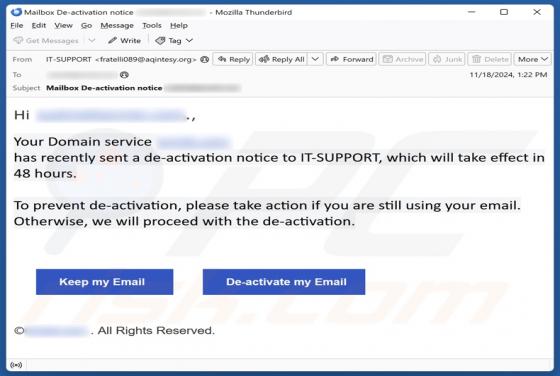
Our analysis confirms that the email is a phishing attempt, pretending to be a notification from DHL (a legitimate logistics company). Its goal is to trick recipients into revealing personal information on a phishing website. Whoever receives this email should ignore it to avoid potential risks.