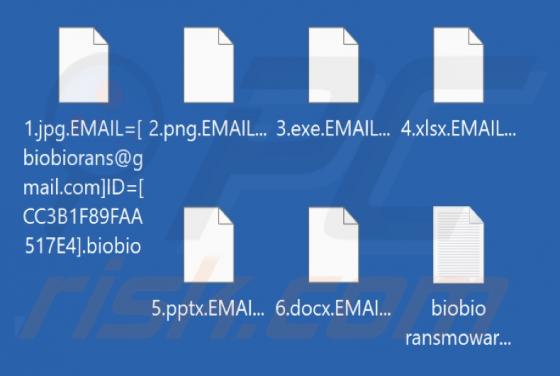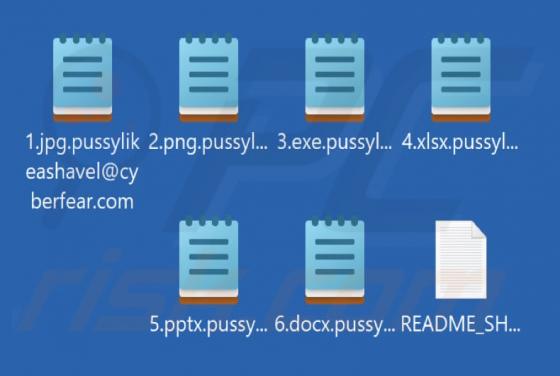
SHAVELP**SY Ransomware
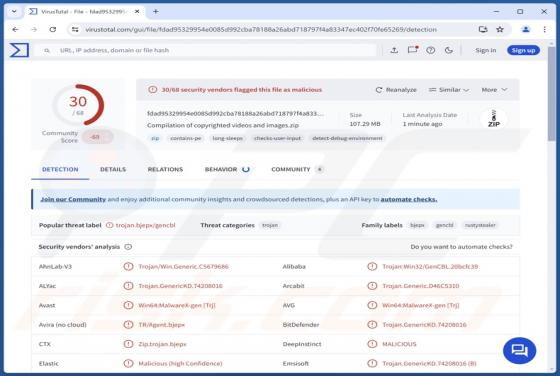
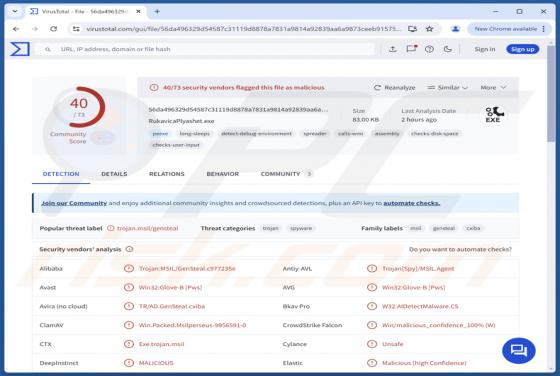
SHAVELP**SY (censored) is ransomware our team discovered while analyzing malware samples uploaded to VirusTotal. We found that it encrypts files, appends the ".p**sylikeashavel@cyberfear.com" extension to filenames, and creates a ransom note ("README_SHAVEL.txt"). An example of how SHAVELP**SY mo