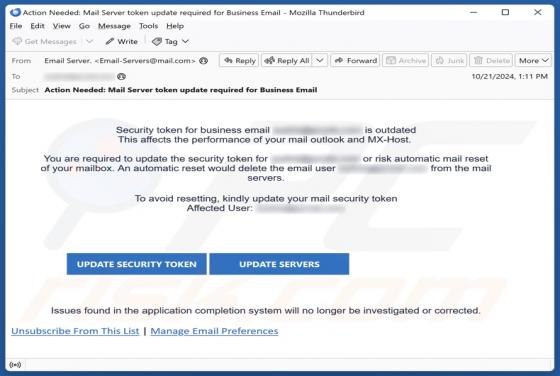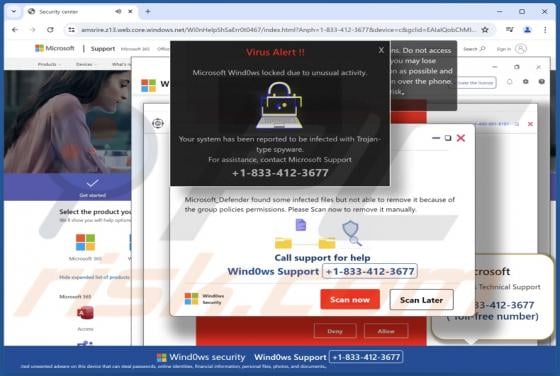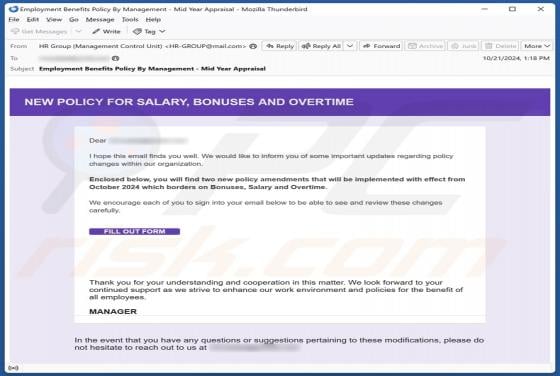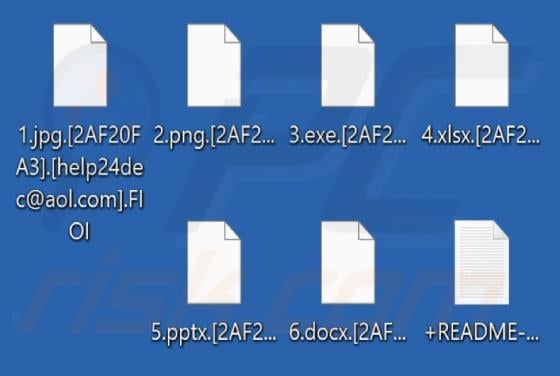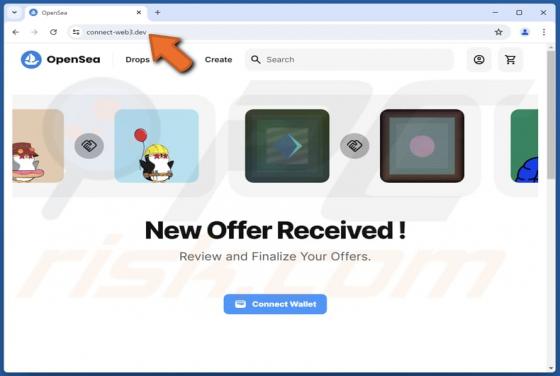
OpenSea NFT Offer Scam
We have inspected the "OpenSea NFT Offer" website (connect-web3[.]dev) and found that it is a scam masquerading as the legitimate OpenSea platform. It is created to trick individuals into taking actions that could lead to significant financial losses. Users should avoid sites like connect-web3[.]d