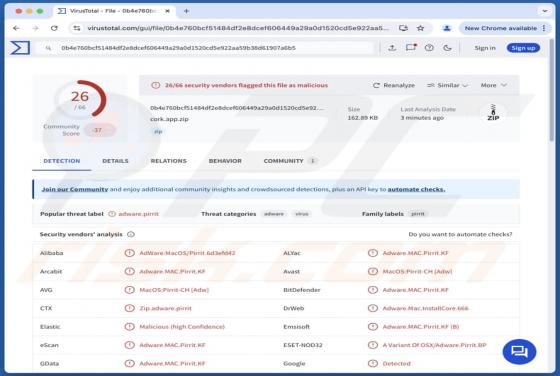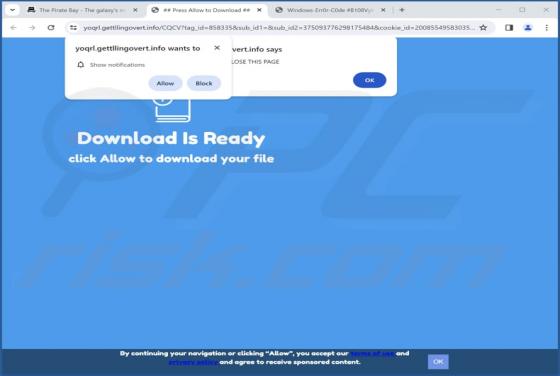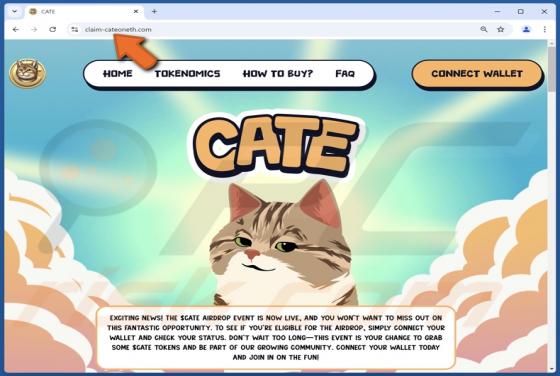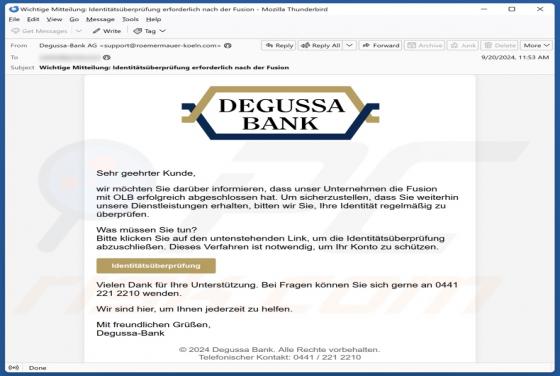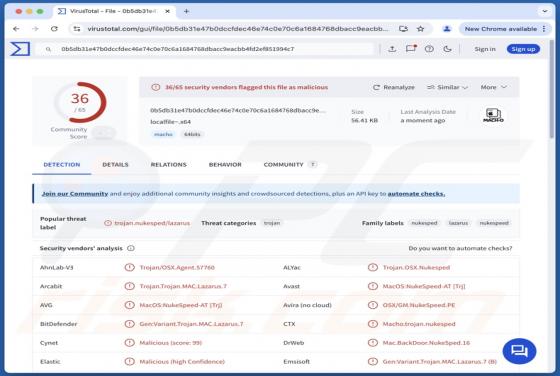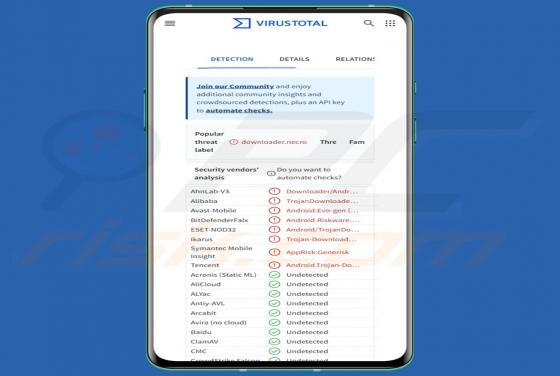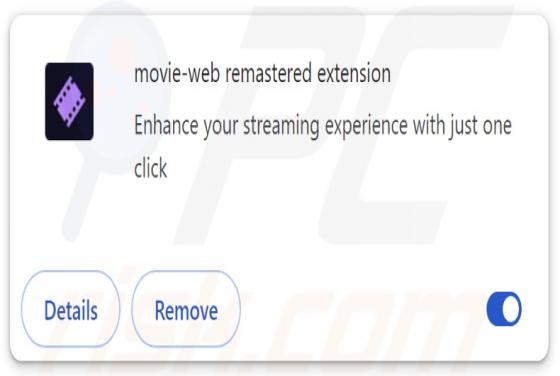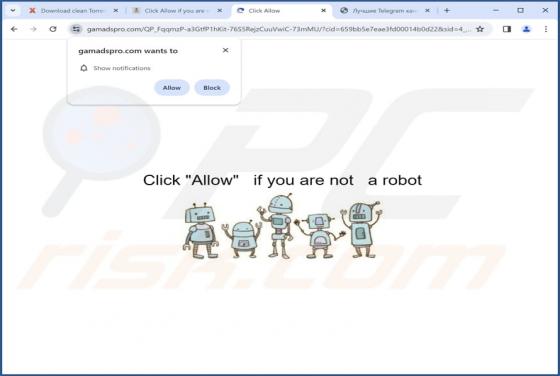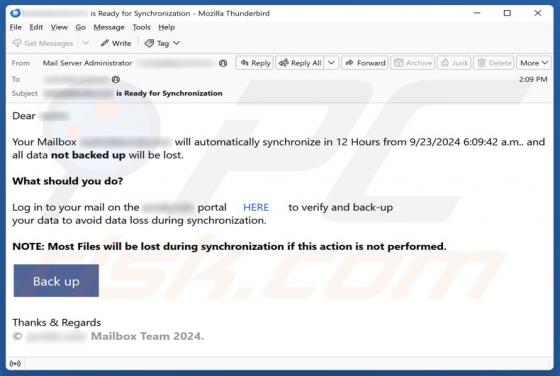
Your Mailbox Will Automatically Synchronize Email Scam
Our team has inspected this email and found that it is written by scammers who attempt to trick recipients into revealing their personal information. Emails of this type fall into the category of phishing emails. Recipients should be aware of phishing attempts and ignore them. This scam em