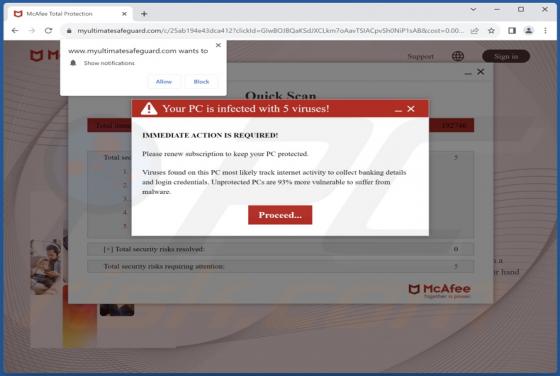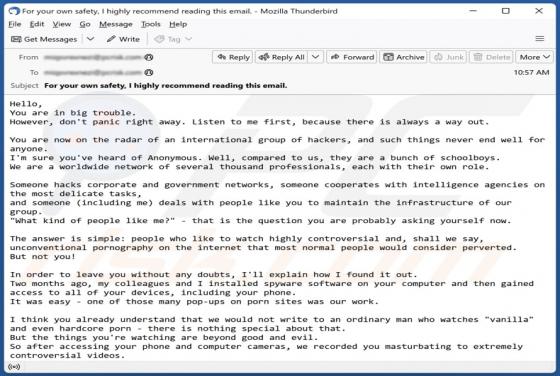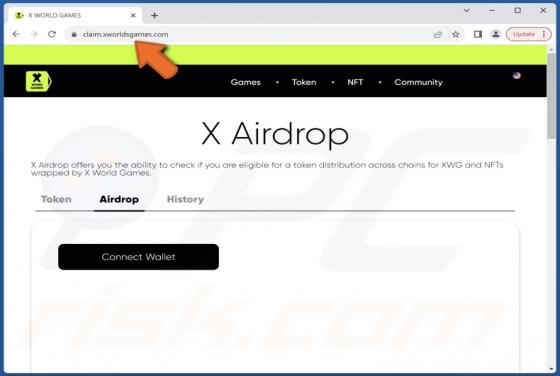
X World Games Airdrop Scam
This "X World Games Airdrop" is a scam. It imitates the legitimate X World Games Web3-type blockchain gaming platform. The scheme claims that eligible users can participate in an XWG token and NFT (Non-Fungible Token) airdrop. However, once a digital wallet is exposed to this scam – a cryptocurren