Unbragging.app Adware (Mac)
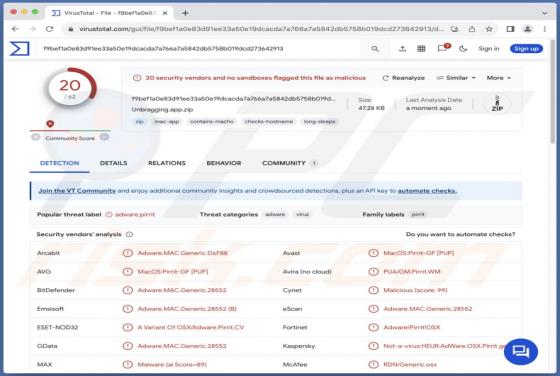
Our examination of the Unbragging.app application revealed its affiliation with the Pirrit family (an adware family), indicating its intent to display intrusive advertisements to users. Additionally, there is a potential risk of Unbragging.app accessing and collecting diverse user data. As a pre