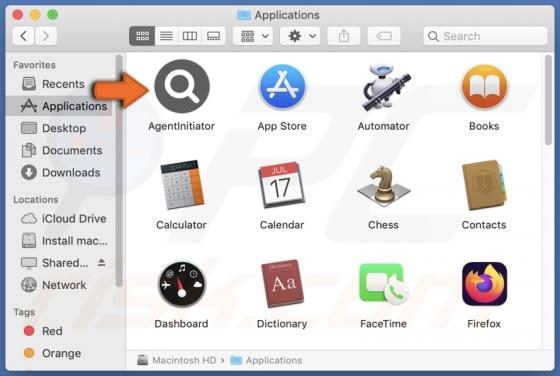
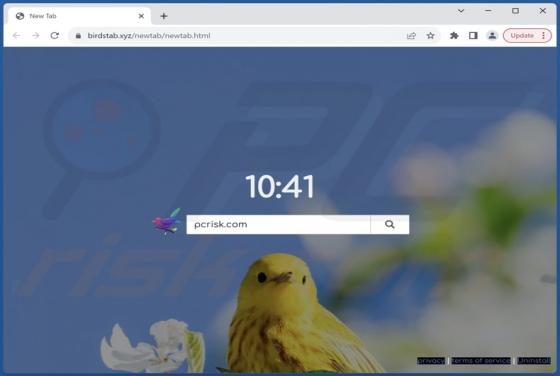
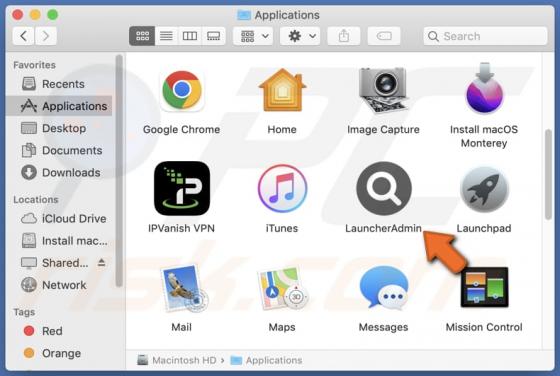
AssistiveArchive Adware (Mac)
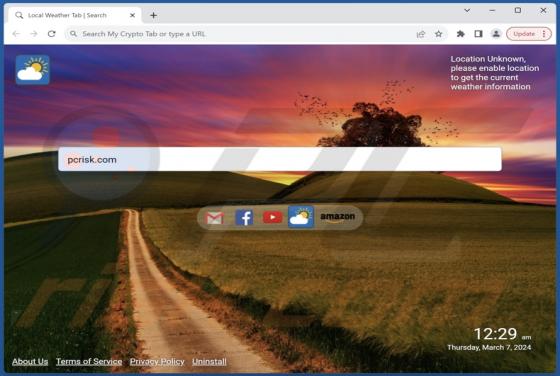
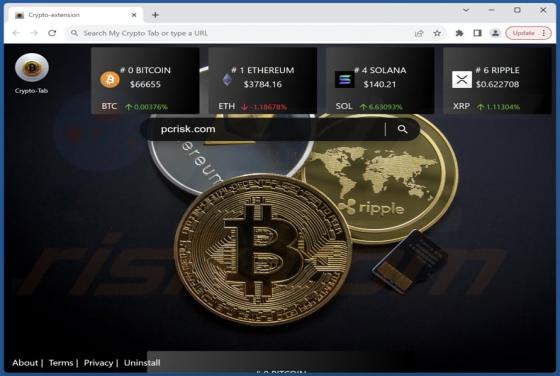
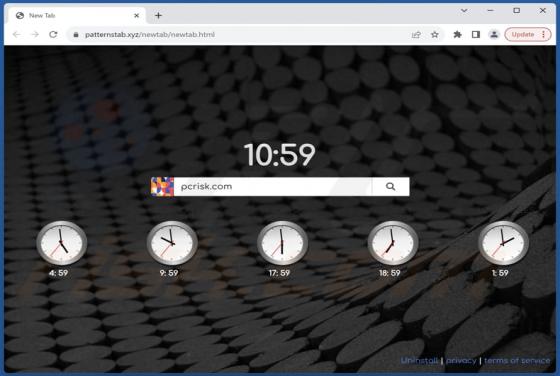
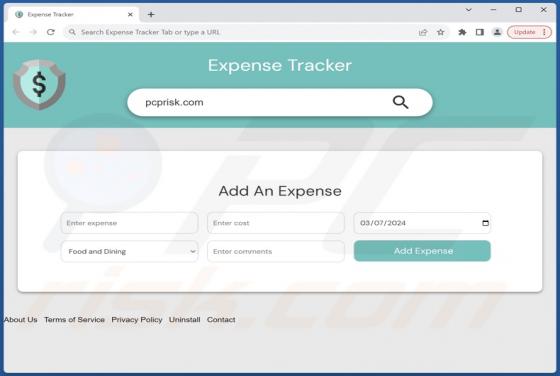
AssistiveArchive is a rogue application classed as adware. We discovered this piece of software while investigating file submissions to the VirusTotal website. AssistiveArchive is part of the AdLoad malware family. It operates by running intrusive advertisement campaigns. Adware stands f