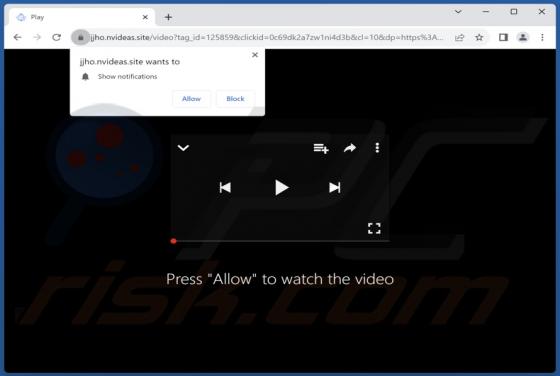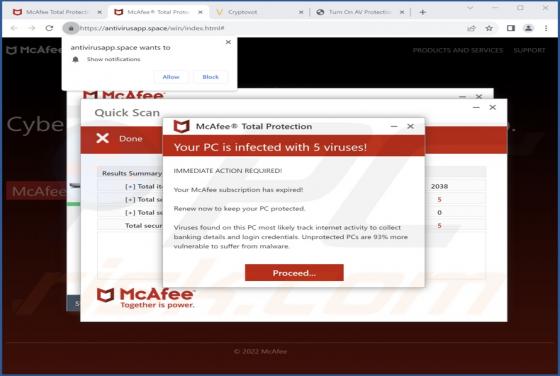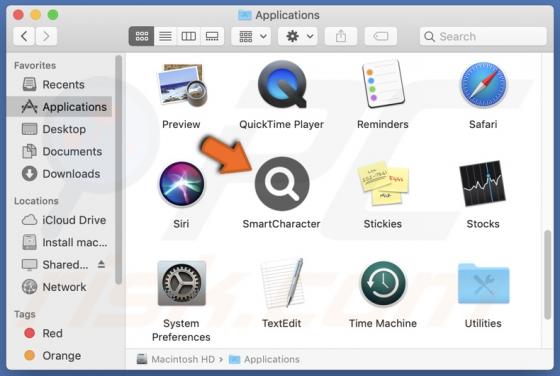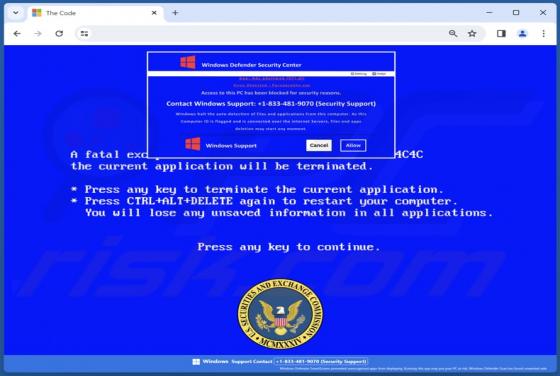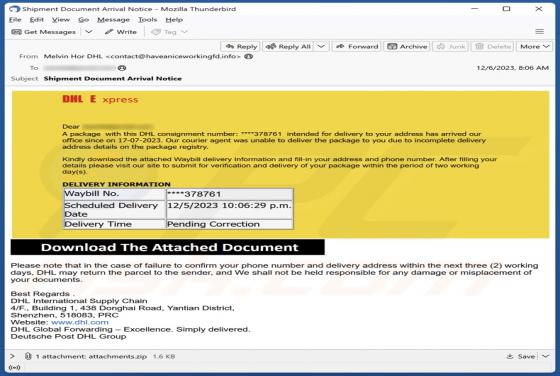
DHL Express - Incomplete Delivery Address Email Scam
After inspecting the "DHL Express - Incomplete Delivery Address" email, we determined that it is fake. This spam letter promotes a phishing scam. It lures recipients into disclosing their email log-in credentials by claiming that their package could not be sent due to an error in the delivery addr