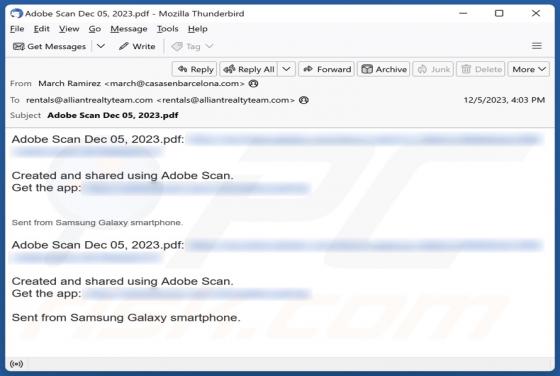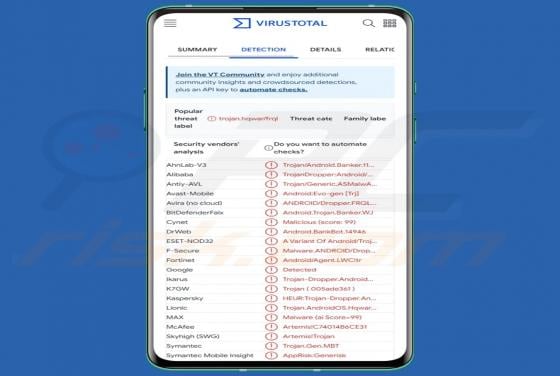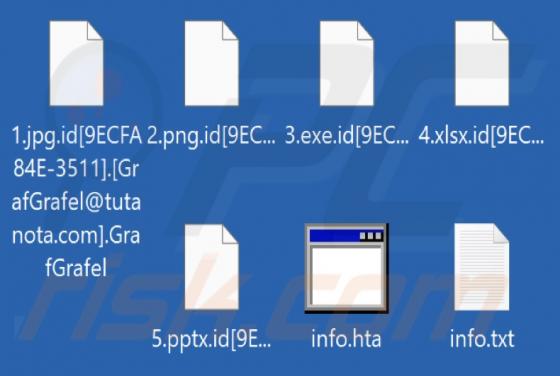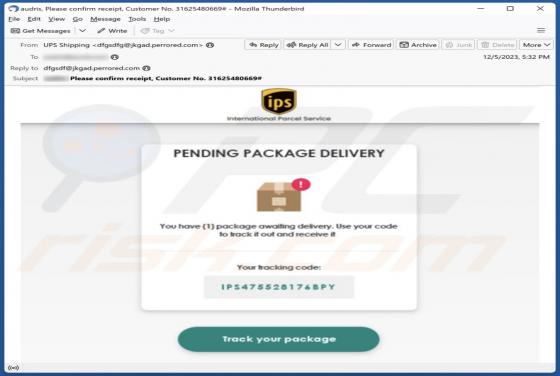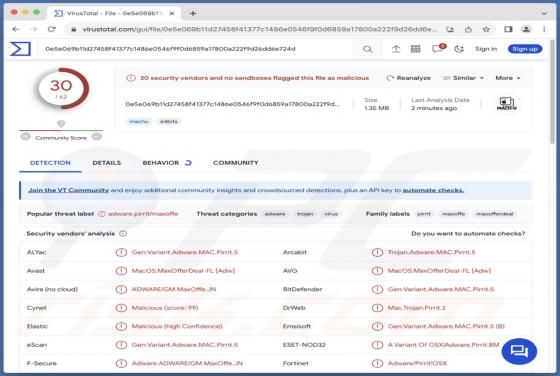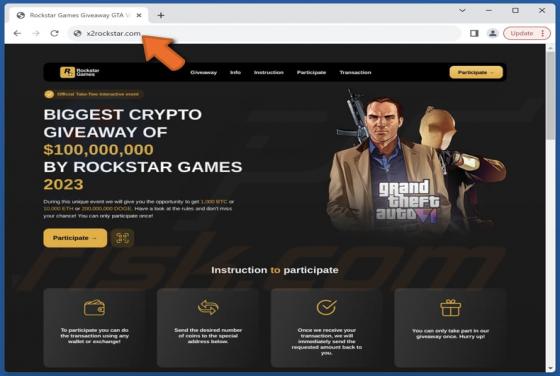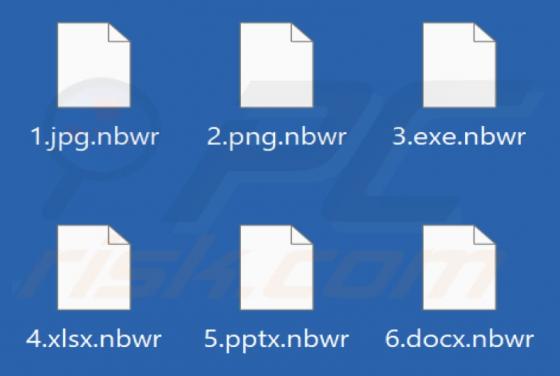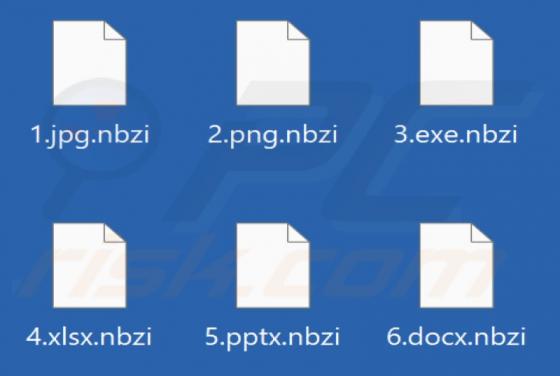
Bestpenad.com Ads
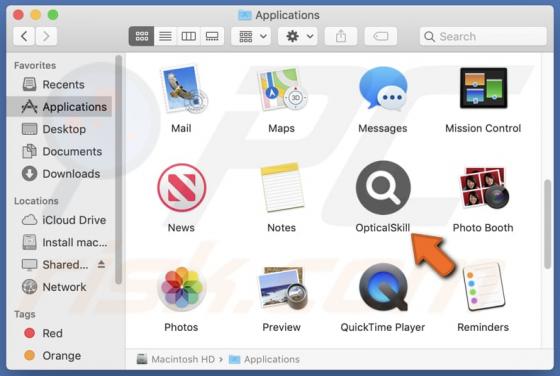
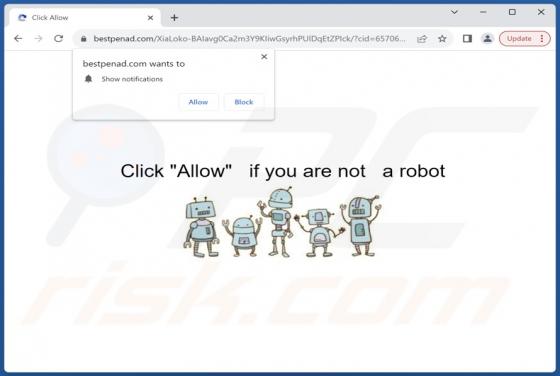
Our researchers found the bestpenad[.]com rogue page during a routine investigation of suspicious websites. Upon inspection, we determined that this webpage promotes browser notification spam and redirects users to other (likely dubious/malicious) sites. Most visitors to bestpenad[.]com and simil