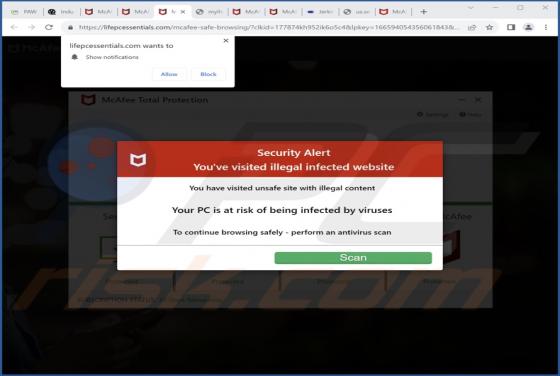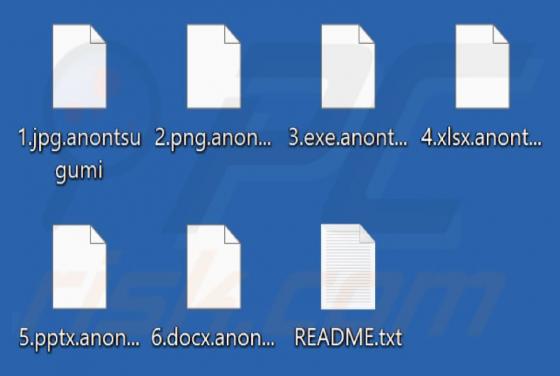
AnonTsugumi Ransomware
While analyzing malware samples uploaded to the VirusTotal website, we discovered ransomware dubbed AnonTsugumi. This malicious program encrypts files, appends the ".anontsugumi" extension to the filenames of the affected files, changes the desktop wallpaper, and provides a ransom note ("README.tx