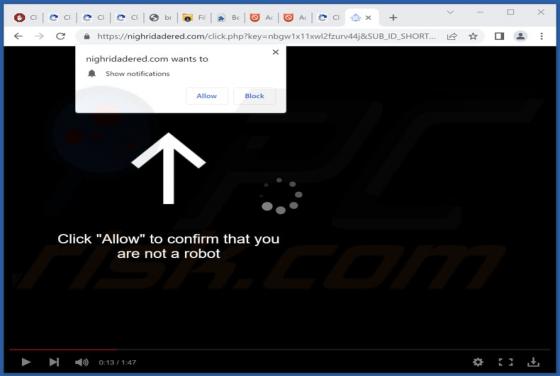
Nighridadered.com Ads
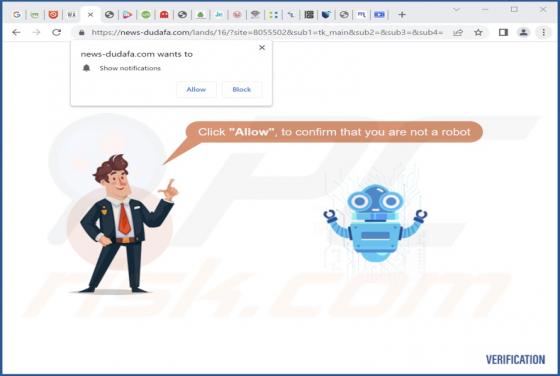
During our investigation of nighridadered[.]com, we found that the website employs a clickbait technique to entice visitors into subscribing to its notifications. Furthermore, nighridadered[.]com may redirect users to unreliable websites. As a result, it is strongly recommended to avoid accessing