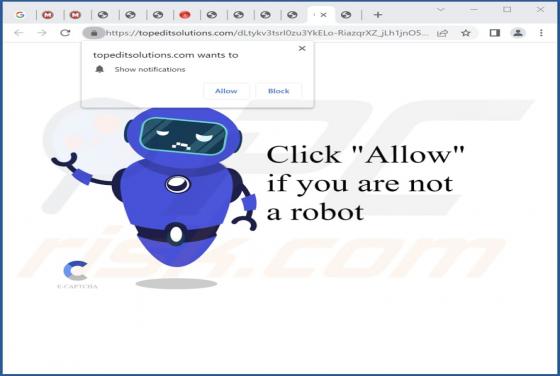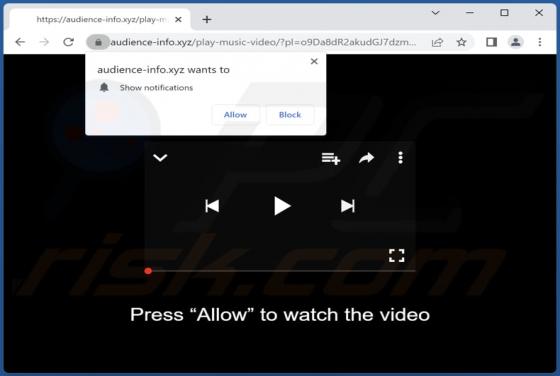
Audience-info.xyz Ads
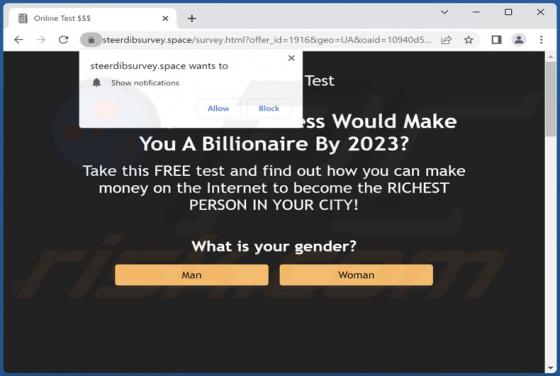
Based on our analysis, audience-info[.]xyz is an untrustworthy website that employs a deceptive tactic to manipulate visitors into subscribing to its notifications. Users typically encounter sites like audience-info[.]xyz unintentionally, and our team came across it during the investigation of oth