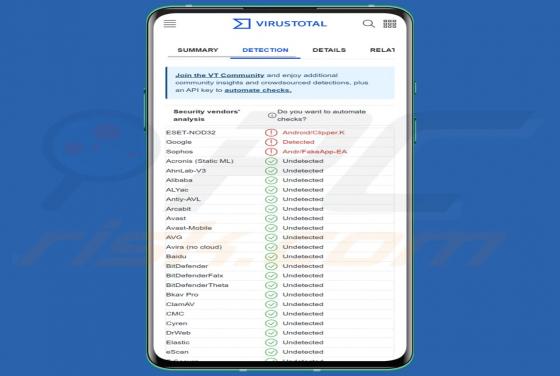
Cryptocurrency Clipper Malware (Android)
A cryptocurrency clipper is a harmful software that can obtain and alter the information stored in the clipboard. ESET has reported numerous fraudulent Telegram and WhatsApp websites which aim to deceive Android (and Windows) users by offering fake (malicious) versions of these messaging applicati