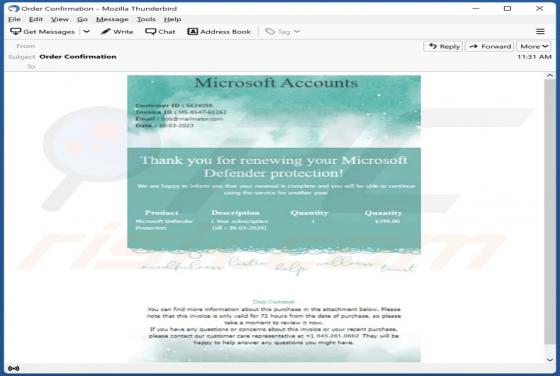
Microsoft Defender Protection Email Scam
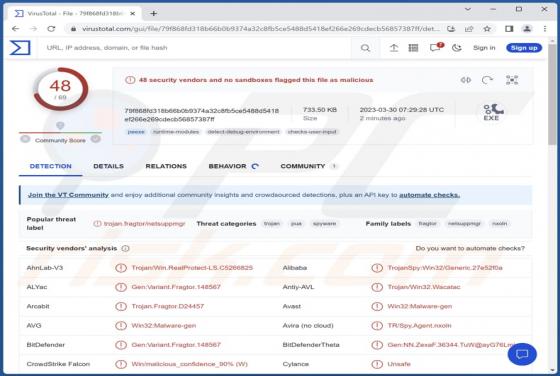
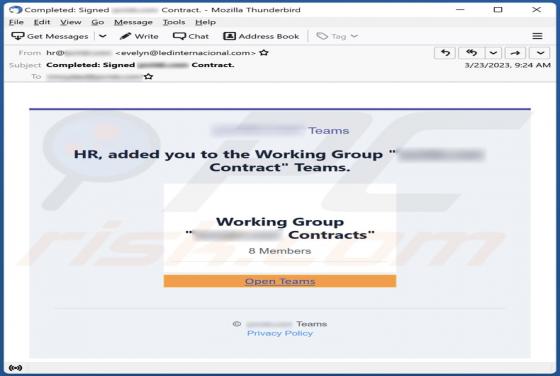
Upon scrutinizing the letter, we have concluded that it is a fraudulent email that has been created by scammers with the intention of tricking recipients into contacting them. The email is disguised as a communication from Microsoft and includes a fake customer support number. We strongly advise r