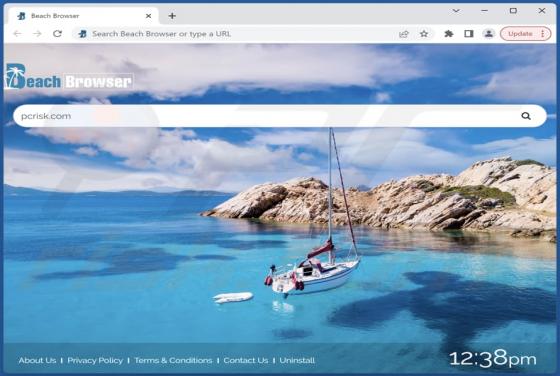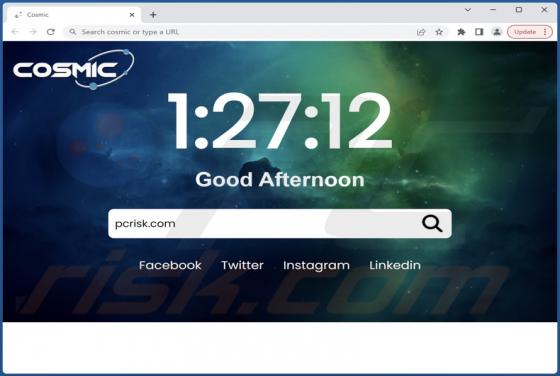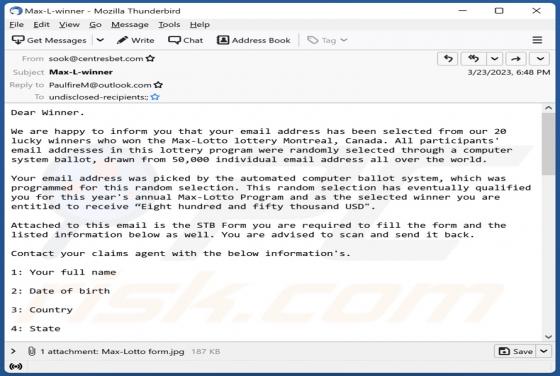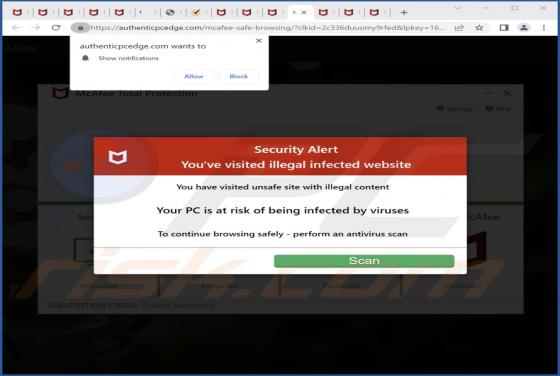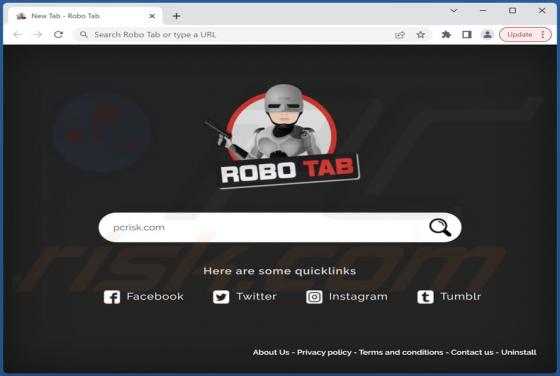
Robo Tab Bowser Hijacker
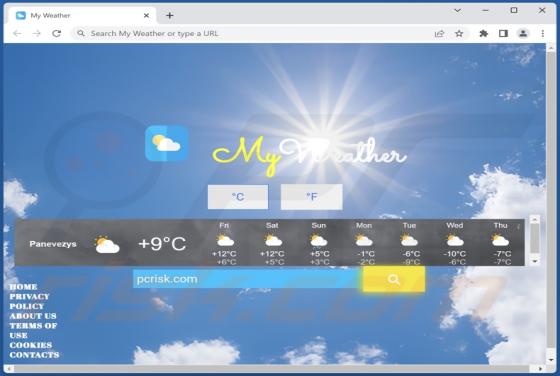
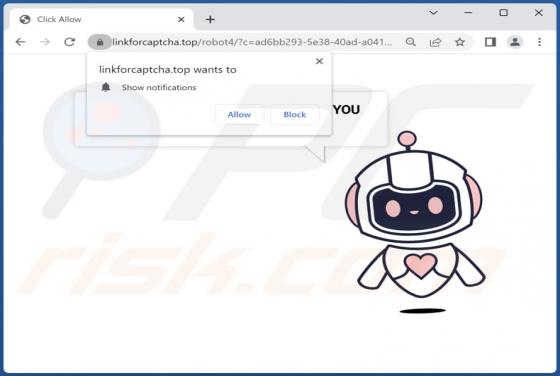
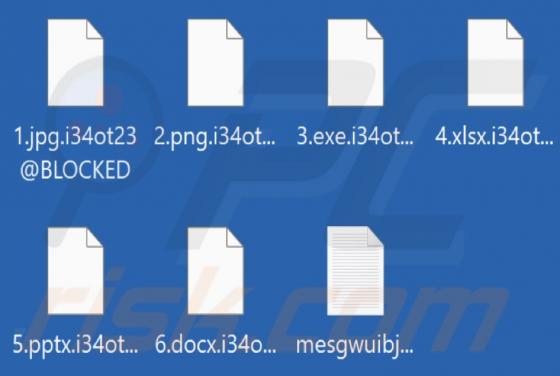
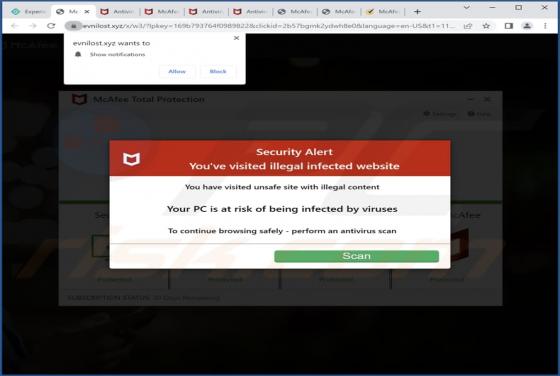
While testing Robo Tab, our team discovered that this browser extension operates as a browser hijacker. The purpose of Robo Tab is to promote search.robo-tab.com (a fake search engine) by changing the settings of a web browser. Additionally, it may gather various data. Thus, it is advisable not to