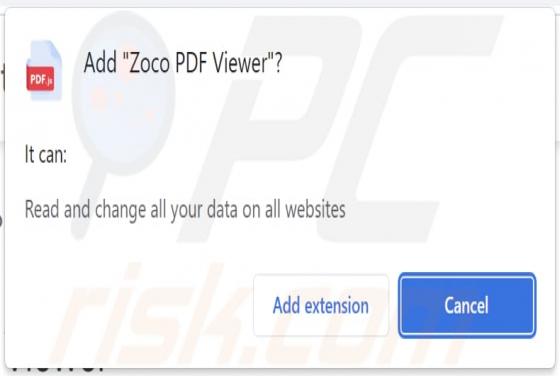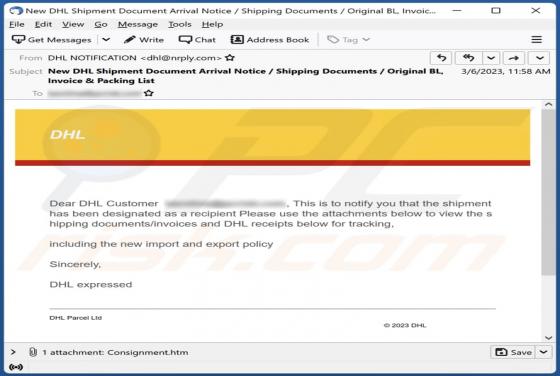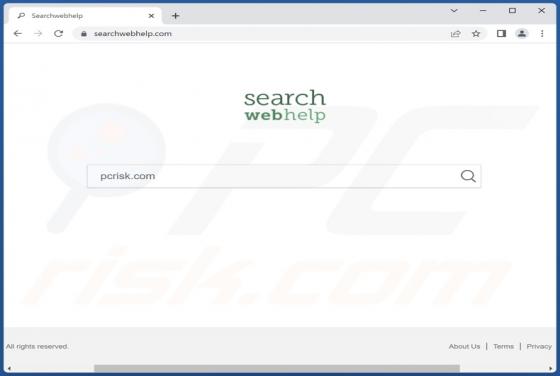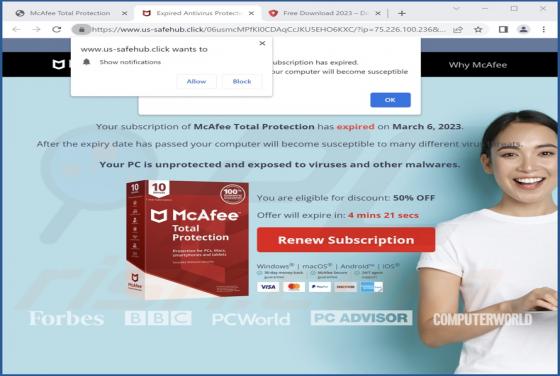
Us-safehub.click Ads
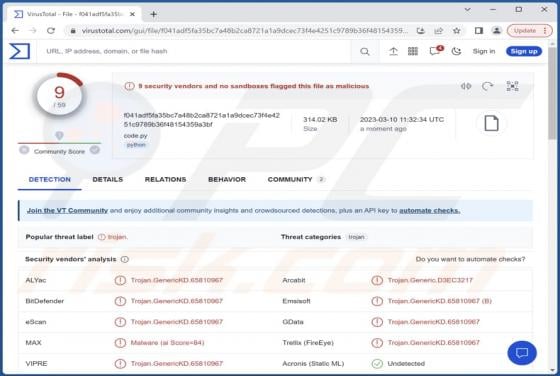
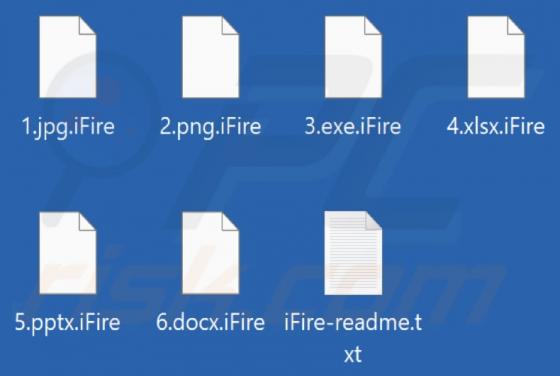
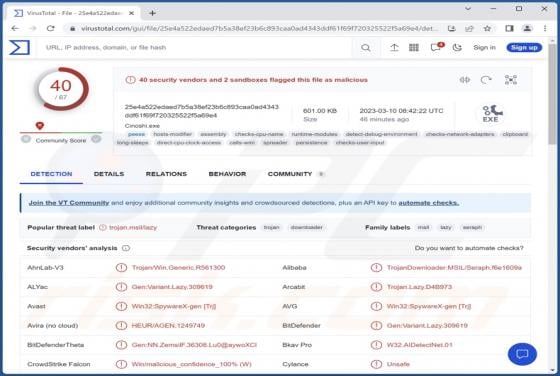
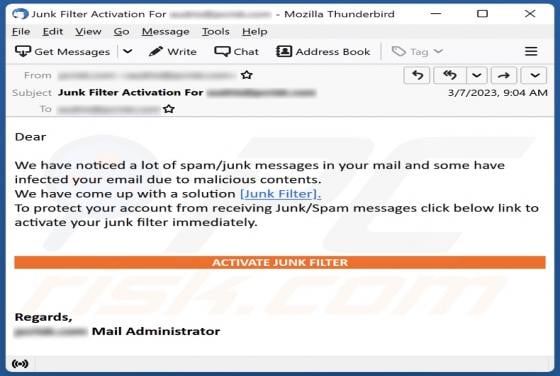
While investigating dubious websites, our research team found the us-safehub[.]click rogue webpage. It is designed to run scams and promote browser notification spam. Furthermore, this page can redirect users elsewhere (likely untrustworthy/harmful) sites. Most visitors to us-safehub[.]click and