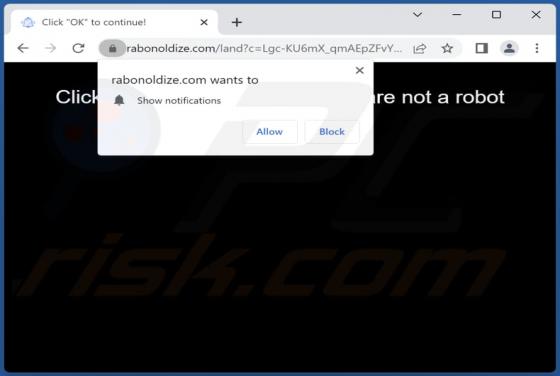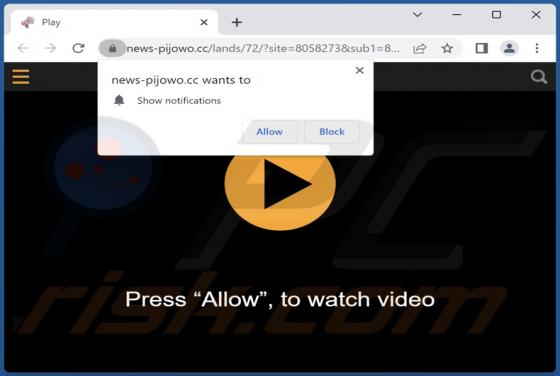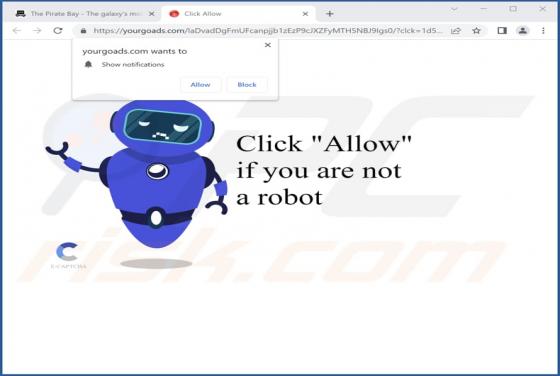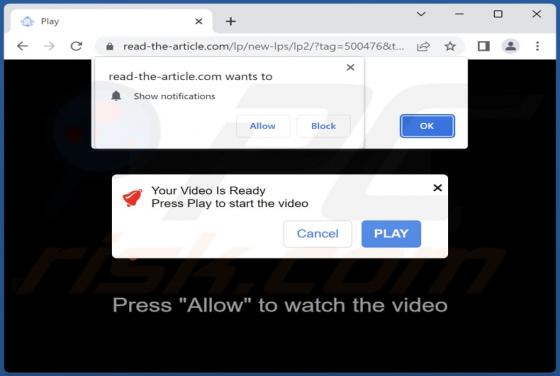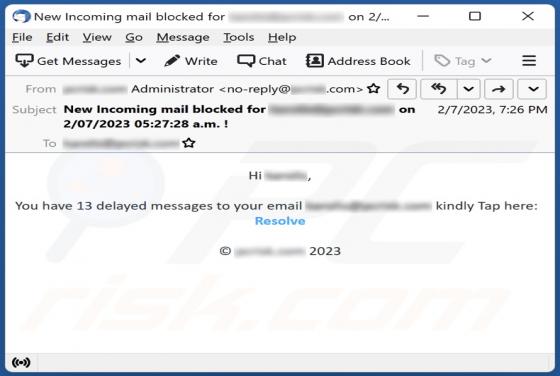
You Have Delayed Messages Email Scam
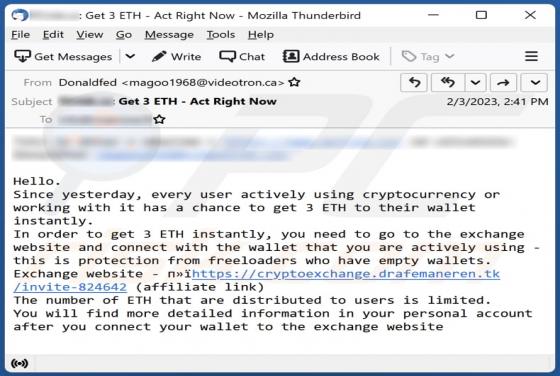
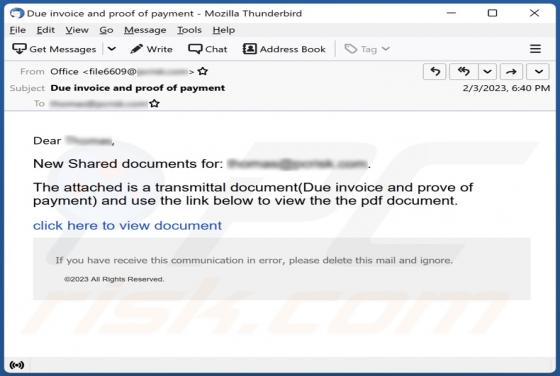
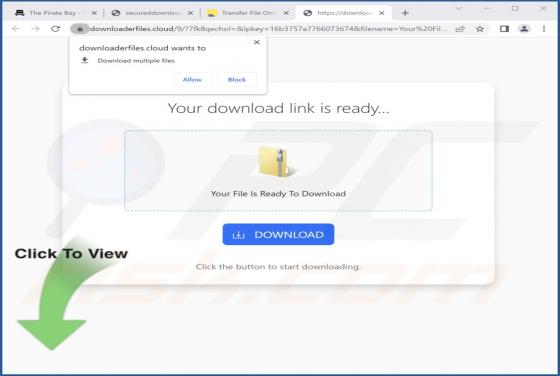
After inspecting the "You Have Delayed Messages" spam email, we determined that it operates as a phishing scam. This letter aims to obtain recipients' email account log-in credentials by making false claims regarding blocked messages. The spam letter with the subject "New Incoming mail blo