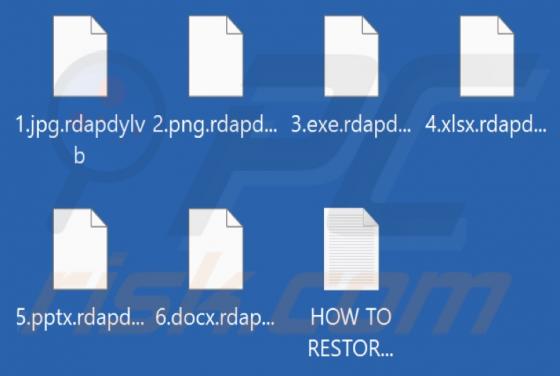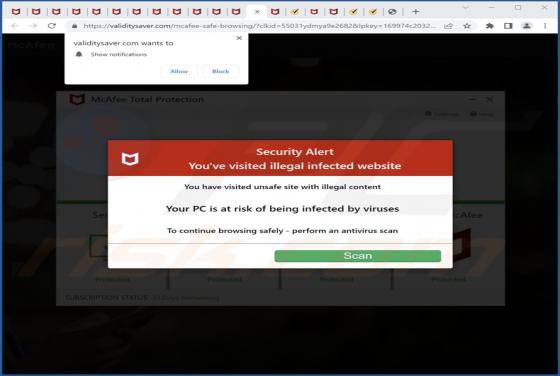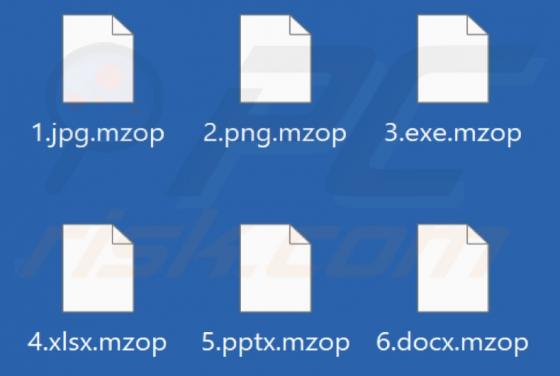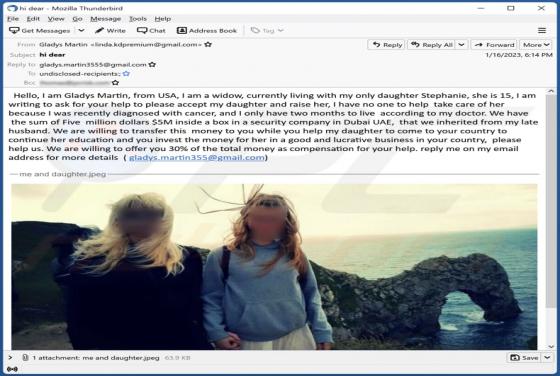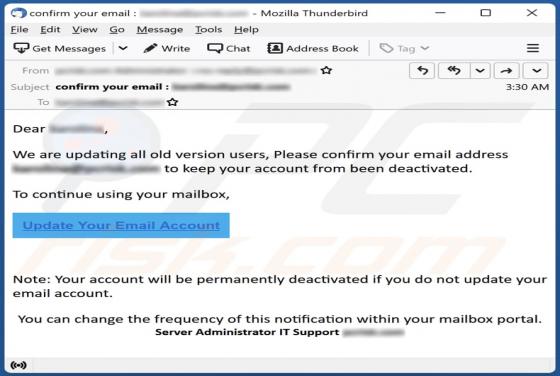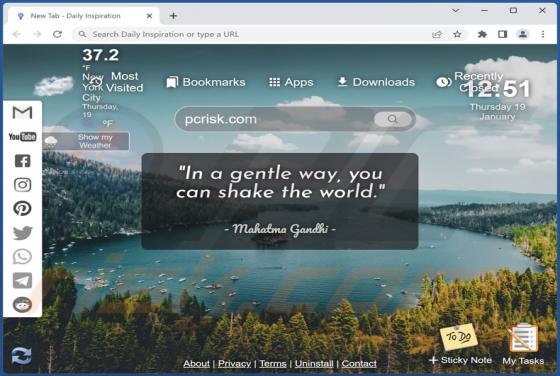
Daily Inspiration Browser Hijacker
Daily Inspiration is the name of a browser extension promising various widgets and features, such as displaying inspirational/motivational quotes, a clock, the weather forecast, sticky notes, and a to-do list on the browser's homepage. Our researchers discovered this piece of software while invest