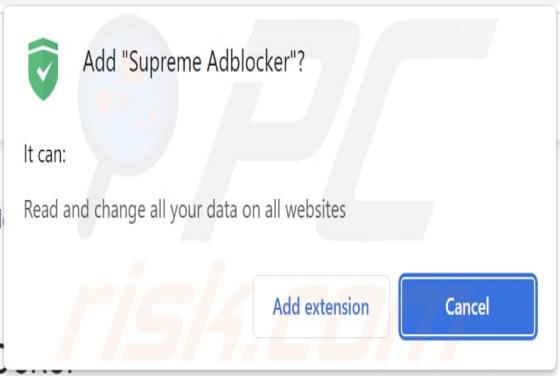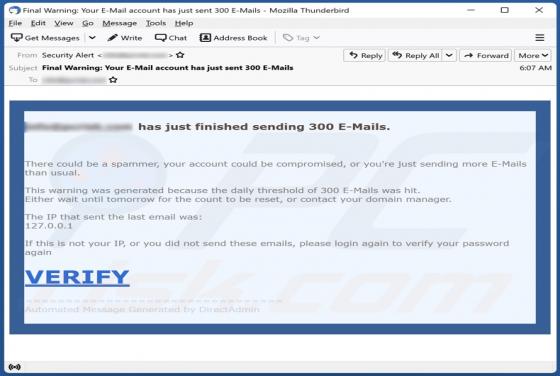
Just Finished Sending 300 E-mails Scam
After inspecting the "Just Finished Sending 300 E-mails" letter, we determined that it is spam. This fake notification informs recipients that their account has been used to send a high volume of emails. The spam letter aims to trick users into providing their email account log-in credentials to a